Orbi LBR20 How-To / Megathread
Forum rules
This forum is for tutorials only--not for help or assistance.
This forum is for tutorials only--not for help or assistance.
Re: Orbi LBR20 How-To / Megathread
FYI, I noticed at some point I broke the OP by accidentally truncating some of the earliest entries in one of my last few updates. Luckily I had a backup so I went back and restored the truncated info. The truncated info was all old stuff which is pretty deprecated by the newer updates but I figured for context and posterity it should be restored.
- These users thanked the author hazarjast for the post:
- Didneywhorl (Tue Dec 14, 2021 4:14 pm)
Re: Orbi LBR20 How-To / Megathread
hazarjast,
Would one implement one or both of these scripts? I use both T-Mobile and AT&T plans with my Orbi LBR20. Is it possible to combine them into one script or is that not recommended?
Thanks!
Would one implement one or both of these scripts? I use both T-Mobile and AT&T plans with my Orbi LBR20. Is it possible to combine them into one script or is that not recommended?
Thanks!
hazarjast wrote: Sun Nov 21, 2021 1:37 am While working on a friend's LBR20 I finally figured out the cause and solution of the ip6tables mangle randomly not taking effect on startup in Voxel's firmware when called using either 'firewall-start.sh' or 'firewall6-start.sh'. It helped that I actually went back and read the man page for the source package that is used for iptables on the LBR20, 'xtables-legacy':
https://manpages.debian.org/testing/ipt ... .8.en.htmlAfter reading that I updated my iptables/ip6tables rules to include '-w' ('--wait') switches and now the ip6tables mangle appears to work on startup as desired. Also realized that for the rare few that have plans provisioned with public IPv4 IPs it would be best to have the iptables rules I was using from the CJ scripts which secure SSH on the WAN interface. Generally not necessary for most since almost all plans are CGNAT'ed these days but still including them for reference below. They all reflect the '-w' switch as indicated:Code: Select all
LIMITATIONS When inserting a rule using iptables -A or iptables -I, iptables first needs to retrieve the current active ruleset, change it to include the new rule, and then commit back the result. This means that if two instances of iptables are running concurrently, one of the updates might be lost. This can be worked around partially with the --wait option.
firewall-start.shfirewall6-start.shCode: Select all
# Secure SSH daemon by ensuring any WAN traffic is blocked iptables -w -C net2loc -p tcp --dport 22 -m state --state NEW -m recent --set > /dev/null 2>&1 || \ iptables -w -I net2loc 1 -p tcp --dport 22 -m state --state NEW -m recent --set # Secure SSH daemon against bruteforce attacks iptables -w -C net2loc -p tcp --dport 22 -m state --state NEW -m recent --update --seconds 60 --hitcount 4 -j DROP > /dev/null 2>&1 || \ iptables -w -I net2loc 1 -p tcp --dport 22 -m state --state NEW -m recent --update --seconds 60 --hitcount 4 -j DROP # IPv4 TTL mod iptables -w -t mangle -C POSTROUTING -o wwan0 -j TTL --ttl-set 65 > /dev/null 2>&1 || \ iptables -w -t mangle -I POSTROUTING 1 -o wwan0 -j TTL --ttl-set 65Code: Select all
# IPv6 TTL mod (prevents leaks not covered by IPv4 rules) # Sleep added for good measure sleep 5 ip6tables -w -t mangle -C POSTROUTING -o wwan0 -j HL --hl-set 65 > /dev/null 2>&1 || \ ip6tables -w -t mangle -I POSTROUTING 1 -o wwan0 -j HL --hl-set 65
Re: Orbi LBR20 How-To / Megathread
Please move or delete if not allowed, I'm not sure where to put this. I have an LBR20 running Voxel with circle jerk and everything running. I also have a Verizon 4G LTE home internet gateway but there is no easy way to add external antennas. I have been trying to just swap sims into the LBR20 but no luck. I have magic done, APN changed, tried changing TTL values in the script but to no avail. I would LOVE for this to work, its showing Band 66 versus Band 2 on ATT that is normally in the Orbi, so its communicating somehow and the signal difference is HUGE... I feel like I'm missing something. It also has a very strange APN and I'm wondering if that is whats causing it. The APN is V5GA01INTERNET, so I first thought it has something to do with the Orbi not being 5G capable, but the Verizon gateway shows "using 4G technology" (or something similar). Am I just missing something? Any help would be great or just a point in the right direction. There is not much info on this Verizon gateway, I wish I could get a 1st gen one because you can add antennas.
Re: Orbi LBR20 How-To / Megathread
Yes, I have it wasn't hard at all. I put it all in an external enclosure.grelm01 wrote: Wed Dec 29, 2021 10:22 pm Has anyone cracked this Orbi open and replaced the U.FL internal LTE antenna's with short U.FL to SMA Fremale to use with a 4x4 mimo antenna?
Re: Orbi LBR20 How-To / Megathread
VOXEL FIRMWARE V9.2.5.2.28S.1F-HW RELEASED
!!! Please upgrade to this version ASAP as there are many security vulnerabilities patched !!!!
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 1SF-HW.zip
Release notes can be found here:
https://www.snbforums.com/threads/custo ... -hw.76775/
Also in this version is 'get-sms.sh' a tool for reading SMS messages. If you can test the tool and report any issues, this would be most appreciated. Usage below:
!!! Please upgrade to this version ASAP as there are many security vulnerabilities patched !!!!
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 1SF-HW.zip
Release notes can be found here:
https://www.snbforums.com/threads/custo ... -hw.76775/
Also in this version is 'get-sms.sh' a tool for reading SMS messages. If you can test the tool and report any issues, this would be most appreciated. Usage below:
Code: Select all
get-sms.sh - read all SMS
get-sms.sh #num - read SMS #num
get-sms.sh #start #end - read SMS from #start to #end.Re: Orbi LBR20 How-To / Megathread
You would use both of the scripts since by default most cellular networks connect with dual stack PDP (IPV4V6) option these days. Voxel recommends splitting them out to segregate iptables commands vs ip6tables commands. Logically I agree with this as it makes sense and easier to troubleshoot later on. Both are called by his netwall script so there's no point in combining them, IMHO.gilbreen wrote: Wed Jan 12, 2022 2:55 pm hazarjast,
Would one implement one or both of these scripts? I use both T-Mobile and AT&T plans with my Orbi LBR20. Is it possible to combine them into one script or is that not recommended?
Thanks!
Re: Orbi LBR20 How-To / Megathread
Unless the 'magic' that has been done matches the VZ gateway device's identifier exactly (and that device is not connected to the network) then nothing else will matter much as I believe the VZ service is IMEI locked. Depending on the firmware you could try switching your MBN file as well but I don't have verizon and have not messed with changing MBN so YMMV.TNdave88 wrote: Thu Jan 20, 2022 9:46 pm Please move or delete if not allowed, I'm not sure where to put this. I have an LBR20 running Voxel with circle jerk and everything running. I also have a Verizon 4G LTE home internet gateway but there is no easy way to add external antennas. I have been trying to just swap sims into the LBR20 but no luck. I have magic done, APN changed, tried changing TTL values in the script but to no avail. I would LOVE for this to work, its showing Band 66 versus Band 2 on ATT that is normally in the Orbi, so its communicating somehow and the signal difference is HUGE... I feel like I'm missing something. It also has a very strange APN and I'm wondering if that is whats causing it. The APN is V5GA01INTERNET, so I first thought it has something to do with the Orbi not being 5G capable, but the Verizon gateway shows "using 4G technology" (or something similar). Am I just missing something? Any help would be great or just a point in the right direction. There is not much info on this Verizon gateway, I wish I could get a 1st gen one because you can add antennas.
Re: Orbi LBR20 How-To / Megathread
Is there a written step by step guide/tutorial for installation of Voxel or other like C?J firmware that can be used with the OEM firmware on a New Orbi LBR20? I just want to apply the magic and TTL so I can use my current sim for ATT. So can I use AT commands and SSH
Re: Orbi LBR20 How-To / Megathread
Voxel is built from open source parts of Netgear firmware but is wholly separate and not iterative when compared to latest OEM firmware versions. The Voxel downloads .zip comes with QuickStart.txt which covers most things. To install Voxel, simply extract the .img file from the .zip, then login to the web GUI and go to 'Advanced > Administration > Firmware Update > Manual Update > Browse' to select the extracted .img file; click Upload and confirm the update allowing time for the upload/flash/reboot to complete. If you are coming from OEM Netgear firmware to Voxel it is recommended that after the unit comes back, you reset it to factory defaults ('Advanced > Administration > Backup Settings > Erase'). Be aware that you will have to go through the initial setup in the web browser again when performing the step.samsil wrote: Mon Jan 24, 2022 12:15 pm Is there a written step by step guide/tutorial for installation of Voxel or other like C?J firmware that can be used with the OEM firmware on a New Orbi LBR20? I just want to apply the magic and TTL so I can use my current sim for ATT. So can I use AT commands and SSH
Once Voxel is installed you will have SSH access. For issuing AT commands in Voxel you simply need to connect to the modem's IP address (192.168.1.1 by default) using Putty or another SSH client and login using user 'root' and the password of the user you have set in the initial configuration (typically the same as the 'admin' password unless you have selected a different username during setup). Once logged in via Putty you have at least a couple of ways to send AT commands to the modem. The most elementary involves simultaneous echo and cat of the AT device ('/dev/ttyUSB2') ex.:
Code: Select all
cat /dev/ttyUSB2` echo -e "AT+EMGR=1,7,\"010101010101010"\r\n" > /dev/ttyUSB2`However, you must be careful to include proper quoting and backticks using cat/echo method and it can be finicky. Therefore the preferred method of sending single commands with immediate return output is echo the commands and pipe to the inbuilt 'microcom' function of BusyBox like so:
Code: Select all
echo -ne "AT+EMGR=1,7,\"010101010101010\"\r\n" | microcom -X -t 1000 /dev/ttyUSB2In regards to TTL, that has been covered many times in this thread (please use the "Search this topic..." function when in doubt), but I'll recap it here below at a high level. First create '/mnt/circle/overlay/opt/scripts' directory if you haven't already then create two files under it (using the text editor of your choice like 'nano' or 'vi'): 'firewall-start.sh' and 'firewall6-start.sh' with the contents as follows:
firewall-start.sh
Code: Select all
# IPv4 TTL mod
iptables -w -t mangle -C POSTROUTING -o wwan0 -j TTL --ttl-set 65 > /dev/null 2>&1 || \
iptables -w -t mangle -I POSTROUTING 1 -o wwan0 -j TTL --ttl-set 65
Code: Select all
# IPv6 TTL mod (prevents leaks not covered by IPv4 rules)
# Sleep added for good measure
sleep 5
ip6tables -w -t mangle -C POSTROUTING -o wwan0 -j HL --hl-set 65 > /dev/null 2>&1 || \
ip6tables -w -t mangle -I POSTROUTING 1 -o wwan0 -j HL --hl-set 65Re: Orbi LBR20 How-To / Megathread
I need help with a little magic....... Please feel free to email me at sean023432@live.com
Re: Orbi LBR20 How-To / Megathread
Sent.Sam023432 wrote: Fri Jan 28, 2022 1:06 pm I need help with a little magic....... Please feel free to email me at sean023432@live.com
-
jonathan_winters
- Posts: 32
- Joined: Tue Apr 14, 2020 8:12 pm
- Has thanked: 1 time
- Been thanked: 8 times
Re: Orbi LBR20 How-To / Megathread
Do you have any stats before and after? I know every location will be different, but just looking for some data as to whether this is a worthwhile upgrade.
Also, I'm very interested to hear about the enclosure and antenna(s) you used - I have some hardware on hand, but I'd really like to compare the info about what has worked for you.
Re: Orbi LBR20 How-To / Megathread
Found there was a unicode conversion bug in 'get-sms.sh' so Voxel has updated it to fix but the updates are not in the firmware yet. For now if you want to use this script I have posted it below. Just create an overlay folder for /usr/bin ('mkdir /mnt/circle/overlay/usr/bin') and copy/paste the content into 'get-sms.sh' there and made it executable ('chmod +x get-sms.sh'). On next reboot, the updated version will be active. Still some testing going on with SMS abilities to be more full-featured and released in a future Voxel firmware but this works well for nowhazarjast wrote: Fri Jan 21, 2022 2:45 pm VOXEL FIRMWARE V9.2.5.2.28S.1F-HW RELEASED
!!! Please upgrade to this version ASAP as there are many security vulnerabilities patched !!!!
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 1SF-HW.zip
Release notes can be found here:
https://www.snbforums.com/threads/custo ... -hw.76775/
Also in this version is 'get-sms.sh' a tool for reading SMS messages. If you can test the tool and report any issues, this would be most appreciated. Usage below:
Code: Select all
get-sms.sh - read all SMS get-sms.sh #num - read SMS #num get-sms.sh #start #end - read SMS from #start to #end.
Code: Select all
#!/bin/sh
PATH=/bin:/sbin:/usr/bin:/usr/sbin
DEVPORT=/dev/ttyUSB2
DNICHAT=/usr/sbin/dnichat
MOBILE_TMP_DIR=/tmp/mobile_tmpfile
MOBILE_TMP_FILE=$MOBILE_TMP_DIR/sms-tmp.txt
MOBILE_OUTPUT_DIR=/tmp/mobile_output
MOBILE_OUTPUT_FILE=$MOBILE_OUTPUT_DIR/sms-utf-8.txt
CONDITION=TRUE
SAVED_DATE=FALSE
stop() {
printf "\033[35m"
printf "─%.0s" $(seq 1 80) | dos2unix | tee -a $MOBILE_OUTPUT_FILE
printf "\n" | dos2unix | tee -a $MOBILE_OUTPUT_FILE
printf "\033[0m"
exit 0
}
# Check if first argument is specified
if [ "x$1" = "x" ]; then
INDEX=1
else
INDEX=$1
fi
# Check if first argument is less then "1"
if [ "$INDEX" -lt "1" ]; then
INDEX=1
fi
# Check if second argument is specified
if [ "x$2" = "x" ]; then
NUM=0
else
NUM=$2
fi
# Create $MOBILE_TMP_DIR if does not exist
if [ ! -d $MOBILE_TMP_DIR ]; then
mkdir $MOBILE_TMP_DIR
fi
# Create $MOBILE_OUTPUT_DIR if does not exist
if [ ! -d $MOBILE_OUTPUT_DIR ]; then
mkdir $MOBILE_OUTPUT_DIR
fi
# Delete output file if exists
if [ -f $MOBILE_OUTPUT_FILE ]; then
rm -f $MOBILE_OUTPUT_FILE
fi
# Set text mode for SMS messages reading
$DNICHAT $DEVPORT "AT+CMGF=1" 2> /dev/null
# Read all SMS messages
while [ "$CONDITION" = "TRUE" ]; do
# Attempt to get SMS message number 'INDEX'
$DNICHAT $DEVPORT "AT+CMGR=$INDEX" 2> $MOBILE_TMP_FILE
CONTENT=$(cat $MOBILE_TMP_FILE)
# Check if SMS message found (i.e. no 'ERROR' in output message)
if [ "x$(printf "$CONTENT" | sed -n '4p' | grep ERROR)" = "x" ]; then
# Check and convert SMS message to UTF-8 codepage if not plain ASCII
SMS=$(printf "$CONTENT" | sed -n '5p' | tr a-z A-Z | dos2unix)
CMP=$(printf "$SMS" | xxd -p -r | xxd -p -c 2048 | tr a-z A-Z | dos2unix)
# Plain ASCII
if [ "$SMS" != "$CMP" ]; then
MSG=$(printf "$CONTENT" | awk "NR >= 5" | head -n -4 | dos2unix)
# Unicode
else
MSG=$(printf "$SMS" | xxd -p -r | iconv -f UTF-16BE -t UTF-8)
fi
# Get SMS date and split output if date is changed (next SMS message)
MSG_DATE=$(printf "$CONTENT" | sed -n '4p' | awk -F "," '{print $4$5}')
if [ "$SAVED_DATE" != "$MSG_DATE" ]; then
printf "\033[35m"
printf "─%.0s" $(seq 1 80) | dos2unix | tee -a $MOBILE_OUTPUT_FILE
printf "\033[1m\033[36m"
printf "\n[Message #%d]\n" $INDEX | dos2unix | tee -a $MOBILE_OUTPUT_FILE
printf "\033[0m\033[33m"
printf "$CONTENT" | sed -n '4p' | dos2unix | tee -a $MOBILE_OUTPUT_FILE
printf "\033[0m"
SAVED_DATE=$MSG_DATE
fi
# Print converted to UTF-8 SMS message
printf "\033[1m"
printf "$MSG\n" | dos2unix | tee -a $MOBILE_OUTPUT_FILE
printf "\033[0m"
# Exit now if only first argument is used
if [ "x$1" != "x" ] && [ "x$2" = "x" ]; then
stop
fi
# Increase SMS message index to read
INDEX=$((INDEX+1))
# Exit now if INDEX greater than second argument
if [ "$NUM" != "0" ] && [ "$INDEX" -gt "$NUM" ]; then
stop
fi
# No SMS messages found
else
if [ "$INDEX" != "1" ]; then
stop
else
printf "No SMS messages found.\n" | dos2unix | tee -a $MOBILE_OUTPUT_FILE
fi
# Exit from the loop
CONDITION=FALSE
fi
done
Re: Orbi LBR20 How-To / Megathread
Hello , i have a question , is there a way to turn off wifi (all 3 radios) ?
Is there a way to switch router in o a bridge mode ? ( connected to LAN device receives a ip from modem).
Is there a way to switch router in o a bridge mode ? ( connected to LAN device receives a ip from modem).
Re: Orbi LBR20 How-To / Megathread
I was just wondering if this setup was still working best for ul/dl speeds with Visible. Currently, I have Voxel installed with magic and ttl mods. But I noticed my speeds aren't what they were with my MR1100 at the moment. (In my case I think it is because I haven't band locked or anything yet and I had to do that on the m1 to get good speeds. If there is a specific guide you used please let me know. I find a lot of them for voxel but not many for CJ.shinesmart wrote: Wed Jul 14, 2021 12:32 pm This comparison was to compare which carrier’s plan is more suited to my needs, that’s why I merely wanted to test them side by side on the same (newest) firmware v2.6.5.2 vs the older v2.5.20. I’ve seen improved speeds on both carriers when running the newest firmware vs the older builds. Here’s the proof via WiFi:
AT&T running 2.6.5.2 yielded 105/40mb
AT&T running 2.5.20 yielded 70/30mb
Visible running 2.6.5.2 yielded 70/25mb
Visible running 2.5.20 yielded 40/15mb
Whilst I’m very interested in the Voxel install, it all comes down to bandwidth speed and reliability. I’m sure his firmware improvements will be very noticeable, but unless it improves the ul/dl speeds, I may opt to stay with the newer stock firmware with CJ, especially if it survives firmware updates.
Very grateful for Voxel’s work as he is a genius and looking forward to testing it.
* BTW, haven’t noticed any throttling by either carrier yet, and I’ve crossed 150gb on each for this month’s cycle. But you are correct, I may have to put up the drapes.
Re: Orbi LBR20 How-To / Megathread
This is the guide I followed to turn off the wifi radios on mine. Credit to hazerjast.
viewtopic.php?p=20064#p20064
viewtopic.php?p=20064#p20064
MiG41 wrote: Mon Feb 07, 2022 2:58 pm Hello , i have a question , is there a way to turn off wifi (all 3 radios) ?
Is there a way to switch router in o a bridge mode ? ( connected to LAN device receives a ip from modem).
Re: Orbi LBR20 How-To / Megathread
Has anyone ever setup the Orbi LBR20 to do load balancing between the LTE and WAN connections? I'm considering trying to set it up but I am not sure the best way to go about doing it. I am considering one of two options.
The first would be to try and create two bridges on the device, one between wwan0 and eth0, and assigning it a static 0.0.0.0 address. The other bridge consisting of the remaining ports already on br0. It would essentially split the device into an Ethernet LTE modem and an access point. With that I could then use something like the TP-Link ER605 to do the load balancing. This is likely the easier solution of the two, but requires additional hardware. I'm thinking it may be as simple as overwriting a few config files but I still have to look into it some more.
The second option doesn't seen viable for now. I was considering mwan3 since the LBR20 is supposed to be OpenWRT based but it doesn't look like the package is installed. I'll have to look into quite a bit more to determine if there is room for mwan3 in the firmware, and if so what is necessary to build my own firmware.
The first would be to try and create two bridges on the device, one between wwan0 and eth0, and assigning it a static 0.0.0.0 address. The other bridge consisting of the remaining ports already on br0. It would essentially split the device into an Ethernet LTE modem and an access point. With that I could then use something like the TP-Link ER605 to do the load balancing. This is likely the easier solution of the two, but requires additional hardware. I'm thinking it may be as simple as overwriting a few config files but I still have to look into it some more.
The second option doesn't seen viable for now. I was considering mwan3 since the LBR20 is supposed to be OpenWRT based but it doesn't look like the package is installed. I'll have to look into quite a bit more to determine if there is room for mwan3 in the firmware, and if so what is necessary to build my own firmware.
Re: Orbi LBR20 How-To / Megathread
Thank you , no more wifi , but i found out , that in top increased Load average: 1.38 1.35 1.33 . I checked the clean version , and i could see , that load average: 0.36, 0.25, 0.34
But i can't see anything with could use cpu so much. Can you check it ?
EDIT:
Looks like not all proceses are stopped and killed ( especially check_status.sh) , when rc.local is used. I gave there even sleep 240 before commands , and still this proces exists, after do the kill command for check_status.sh manual from ssh load dropped. Any idea why it is not possible ( or how to do it) to kill check_sttus.sh from script ?
But i can't see anything with could use cpu so much. Can you check it ?
EDIT:
Looks like not all proceses are stopped and killed ( especially check_status.sh) , when rc.local is used. I gave there even sleep 240 before commands , and still this proces exists, after do the kill command for check_status.sh manual from ssh load dropped. Any idea why it is not possible ( or how to do it) to kill check_sttus.sh from script ?
-
jonathan_winters
- Posts: 32
- Joined: Tue Apr 14, 2020 8:12 pm
- Has thanked: 1 time
- Been thanked: 8 times
Re: Orbi LBR20 How-To / Megathread
I was looking at this for something completely unrelated to my LBR20's network, but this device supports the "ip" command for adding/editing your routing, so something like this should work:chiaworld wrote: Tue Feb 15, 2022 9:43 pm Has anyone ever setup the Orbi LBR20 to do load balancing between the LTE and WAN connections? I'm considering trying to set it up but I am not sure the best way to go about doing it. I am considering one of two options.
https://lartc.org/howto/lartc.rpdb.multiple-links.html
It doesn't give you an exactly perfect load balance, but it should work. And if one is consistently faster than the other, you could adjust the weights accordingly such that you're directing proportionally more traffic through the faster connection.
Just be careful - adding an incorrect route can lock you out of your device. It isn't a huge deal because a reboot will clear the routes and reset it to the default. But if you're in an environment where rebooting your router (or downtime in general) is not acceptable then you'll want to test this on another system before you begin.
Once you have it figured out, you'll need to leverage one of the scripts to have your device create the routes on reboot. I'd maybe add a delay so that if something goes wrong with the routes in the future, you have a period of time after a reboot but before the routes are added when you can log in and disable these. (In that time, you'd presumably still have connectivity; it just wouldn't be load-balanced.)
Re: Orbi LBR20 How-To / Megathread
I'm getting a "400 Bad Request" using the web GUI. Has anyone else came across this? I came across a post on the official Netgear forums, and they suggest to do a "hard reset". I would really like to avoid that if possible. I am running Voxel firmware with some edits.
Re: Orbi LBR20 How-To / Megathread
Hoe does one check the CPU load of the device?
MiG41 wrote: Wed Feb 16, 2022 2:18 am Thank you , no more wifi , but i found out , that in top increased Load average: 1.38 1.35 1.33 . I checked the clean version , and i could see , that load average: 0.36, 0.25, 0.34
But i can't see anything with could use cpu so much. Can you check it ?
EDIT:
Looks like not all proceses are stopped and killed ( especially check_status.sh) , when rc.local is used. I gave there even sleep 240 before commands , and still this proces exists, after do the kill command for check_status.sh manual from ssh load dropped. Any idea why it is not possible ( or how to do it) to kill check_sttus.sh from script ?
Re: Orbi LBR20 How-To / Megathread
Since folks keep installing my old circle_jerk mod on top of Voxel and gumming up the works I've removed all references to CJ in the OP. The relevant pieces of CJ info were moved to its github page for posterity.
- These users thanked the author hazarjast for the post:
- Didneywhorl (Wed Mar 09, 2022 12:00 pm)
Re: Orbi LBR20 How-To / Megathread
Is there any additional detail on this post? I have an NBR750 I would love to try this firmware on. I attempted to upload the LBR20 but it won't take it.
hazarjast wrote: Wed Nov 03, 2021 1:25 pm Voxel firmware V9.2.5.2.26SF has been released. Mostly package updates with some fixes as well. OP updated with download and release notes links.
Also, the successor to the LBR20 with WiFi 6 (though not the newer 6e standard) and 5G is now being sold by Netgear: https://www.netgear.com/home/wifi/mesh/nbk752/
(NBR750 is the actual model number of the router unit; FCC ID PY320400511)
Unfortunately they force you to buy it in a pack with an additional Orbi satellite and the package price is an eye-watering $1100 USD on pre-order. The good news is that it appears they stuck with Quectel for the modem (specifically the RM502Q-AE) so much of the same stuff in this thread should likely apply to it as well. I will definitely not be purchasing one at the astronomical MSRP though so I do not plan on posting anymore about it in this thread.
For those curious...
User manual can be found here: https://www.downloads.netgear.com/files ... _UM_EN.pdf
FCC filing docs on the router itself can be found here (no good pics until December though, it appears): https://fcc.report/FCC-ID/PY320400511
FCC filing docs on the Quectel modem used by the router can be found here: https://fcc.report/FCC-ID/XMR2020RM502QAE
Quectel Hardware Guide for the modem can be found here: https://fcc.report/FCC-ID/XMR2020RM502QAE/5019309
Re: Orbi LBR20 How-To / Megathread
Nothing additional yet. Voxel is only creating firmware for the LBR20 not for the NBR750. Not sure if/when NBR750 would receive aftermarket firmware. I do know a few folks playing with them but no full firmware built for them at this time. Due to the crazy high retail cost of the NBR750 and the fact that it just contains a Quectel RM502Q-AE, I have started a new modem build using that same modem and a Raspberry Pi 4 as an OpenWRT host for it to be used via ModemManager. I will cross-post a link to that project once it is ready for others to view ittekwarren wrote: Wed Mar 09, 2022 2:42 pm Is there any additional detail on this post? I have an NBR750 I would love to try this firmware on. I attempted to upload the LBR20 but it won't take it.
If I hear anything in regards to custom firmware for the NBR750 I will be sure to share but nothing like this exists at present time.
Re: Orbi LBR20 How-To / Megathread
I created a new post under Tutorials which links to my 5G build for those interested: viewtopic.php?t=3450
Re: Orbi LBR20 How-To / Megathread
Updated OP with link to latest Voxel firmware.
This may be the last update for awhile due to the current geopolitical events going on in Voxel's region of the world: https://www.snbforums.com/threads/voxel ... tus.77704/
This may be the last update for awhile due to the current geopolitical events going on in Voxel's region of the world: https://www.snbforums.com/threads/voxel ... tus.77704/
Re: Orbi LBR20 How-To / Megathread
So I managed to push through the troubles I was having with TTL on my LBR20, but now I’m having a new issue. Every time I reboot the unit it won’t connect to the internet.
Thanks for any help. This has been absolutely maddening.
Thanks for any help. This has been absolutely maddening.
You do not have the required permissions to view the files attached to this post.
Re: Orbi LBR20 How-To / Megathread
After reboot if I change the APN to fbb.home or wholesale (fast.t-mobile.com never works) depending completely on what was used prior to reboot, it connects instantly.
Essentially if I flip flop between the two APNs on reboot it will reconnect to Internet. But nothing else works to get it up again, other than this.
Very strange.
Essentially if I flip flop between the two APNs on reboot it will reconnect to Internet. But nothing else works to get it up again, other than this.
Very strange.
Re: Orbi LBR20 How-To / Megathread
I am having a very similar issue, but with the ATT tablet plan. I posted in this thread originally, but found a specific Orbi troubleshooting section and moved my post there. You may want to do the same.BigRed wrote: Sat Mar 19, 2022 11:54 am After reboot if I change the APN to fbb.home or wholesale (fast.t-mobile.com never works) depending completely on what was used prior to reboot, it connects instantly.
Essentially if I flip flop between the two APNs on reboot it will reconnect to Internet. But nothing else works to get it up again, other than this.
Very strange.
viewtopic.php?p=24090#p24090
Re: Orbi LBR20 How-To / Megathread
Believe we sorted your issue via the Facebook group with a proper hard reset of the device via the hardware reset button on the back of the unit. If this is not the case please let me know.BigRed wrote: Sat Mar 19, 2022 10:36 am So I managed to push through the troubles I was having with TTL on my LBR20, but now I’m having a new issue. Every time I reboot the unit it won’t connect to the internet.
Thanks for any help. This has been absolutely maddening.
Re: Orbi LBR20 How-To / Megathread
Yes, this is good advice. Did not realize there was a troubleshooting section for Orbi. It will be good to post for help there to give more eyes to the issue. I replied to your post with some questions.egauk wrote: Mon Mar 21, 2022 11:33 am
I am having a very similar issue, but with the ATT tablet plan. I posted in this thread originally, but found a specific Orbi troubleshooting section and moved my post there. You may want to do the same.
viewtopic.php?p=24090#p24090
Re: Orbi LBR20 How-To / Megathread
Updated OP with link to latest Voxel firmware. It seems he is still managing to provide updates despite the ongoing conflict. For this I am quite thankful 
VOXEL FIRMWARE V9.2.5.2.29.1SF-HW RELEASED
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 2.29.1.zip
Release notes can be downloaded here:
https://www.voxel-firmware.com/Download ... 1SF-HW.log
Re: Orbi LBR20 How-To / Megathread
This post will serve to store the historical info originally present in the OP. It is here for posterity only and presents outdated info and instructions which SHOULD NOT be used.
------------------------------------------------------------------------------------------------------------------------------------------------------
VOXEL FIRMWARE V9.2.5.2.29.1SF-HW RELEASED
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 2.29.1.zip
Release notes can be downloaded here:
https://www.voxel-firmware.com/Download ... 1SF-HW.log
VOXEL FIRMWARE V9.2.5.2.29SF-HW RELEASED
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 9SF-HW.zip
VOXEL FIRMWARE V9.2.5.2.28S.1F-HW RELEASED
!!! Please upgrade to this version ASAP as there are many security vulnerabilities patched !!!!
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 1SF-HW.zip
Release notes can be found here:
https://www.snbforums.com/threads/custo ... -hw.76775/
Also in this version is 'get-sms.sh' a tool for reading SMS messages. If you can test the tool and report any issues, this would be most appreciated. Usage below:
***VOXEL V9.2.5.2.23.1SF-HW***
Voxel has made a new revision already which includes improved QCA WiFi drivers taken from Netgear stock v2.6.5.2. This should improve WiFi performance for those that use WiFi on the LBR20:
https://www.voxel-firmware.com/Download ... 1SF-HW.zip
This was done for the RBK50 as well. More details can be found here;
https://www.snbforums.com/threads/custo ... ost-700398
***VOXEL FIRMWARE IS HERE!***
https://www.voxel-firmware.com/Download ... 3SF-HW.zip
That's right folks! The legend himself has applied his optimization skillz to the LBR20. Being the first Voxel release for the LBR20 I would like get as many LBR20 owners who can test it as possible so we can provide valuable feedback and support for future revisions. Also, please consider donating some $$$ if you are are happy with his work as I know for a fact he had to pay over $650 USD of his own money in his country to obtain an LBR20 in order to compile firmware for it. This has not yet been announced in the SNB forums as he would like some extended testing which I told him we would be happy to provide
Netgear's latest stock firmware (2.6.4.2+) includes more encryption for Netgear's internal HTTPS certs which makes the source firmware harder to work with and it provides no real feature enhancements. Thus, this first release is based off of the popular 2.5.2.20 stock firmware GPL sources and has been tested to run just fine with A05 and A06 LTE (Quectel) modem firmware (tested by me on T-Mobile/Sprint). Because it is built on 2.5.2.20 source, it is recommend to flash to Netgear 2.5.2.20 prior to flashing Voxel's firmware otherwise softbrick could occur requiring TFTP recovery (https://kb.netgear.com/000059634/How-to ... ndows-TFTP).
Voxel firmware V9.2.5.2.23SF enhancements vs Stock:
***UPDATES REGARDING LATEST ROUTER FW v2.6.3.50 AND LTE FW A06***
As my last update from 2/18 indicated, router firmware v2.6.3.50 made some significant changes, chiefly disabling the ability to make changes on '/mnt/ntgr/...' which are reboot-persistent. Aside from the new router firmware version there is also a new LTE (Quectel modem) firmware version, A06. This modem firmware update was much more helpful than the router firmware as it appears to have improved modem stability on T-Mobile for me along with allowing the modem to connect to B41, which I did not see it do successfully before (B41 LTE may not be available in all markets). It works perfectly fine paired with 2.5.2.20 router firmware in my testing.
Digging into v2.6.3.50
Netgear seems to have finally stepped up their security game in fw v2.6.3.50 and, while that's a good thing in general, it has made modding a bit more difficult. As many have noticed already, the 'debug.htm' page with the checkbox for enabling telnet was removed and classic Netgear 'telnetenable' utilities do not work to enable telnet on this newer firmware either. This brings the LBR20 in line with the Orbi flagship products as most of those already lost [easy] telnet abilities in 2020 already. So, I had to crack open my dev unit and look for the jumper terminal pins I found while disassembling my original unit to see if they were indeed UART for accessing a serial console. After some fiddling with the pins and a multimeter I was off to the races at 115200 baud with an FTDI cable.
I was initially met with some frustration due to having TX and Ground reversed (and thus not being able to get any response to my keyboard inputs) but once I got that sorted I was greeted with a familiar Chaos Calmer root shell. From there I was able to confirm some relevant pieces of information that have changed in this new firmware. I won't list all my findings here but only those which are germane to our modem and iptables modding efforts:
Other Goodies Found
Found some other 'hidden' goodies so far in the new firmware web interface as well. Here is an inventory that might be worth further exploration by folks who have the time and/or interest:
***IMPORTANT NOTE 02/18/21***
Coming out of hibernation for a moment to post a warning for Netgear LBR20 owners: the latest firmware (2.6.3.50) appears to change the partition structure making the Armor partition used to bootstrap custom scripts non-reboot-persistent. Also, telnet is not as easy to enable. I don’t have time to spend on engineering a solution to resolve this at present so recommend staying on older firmware for now. Can’t say I didn’t warn you . You can find the 2.5.2.20 firmware here in case Netgear pulls it but be aware that the filesystem changes that occur when moving beyond this version do not revert and '/mnt/ntgr/...' changes will still not persist on reboot unless you make some further partition modification manually:
https://drive.google.com/file/d/1Tc09ja ... sp=sharing
Finally, some of my original assumptions were wrong such as the unit not having serial terminal software installed (it does in fact have 'minicom'). I am leaving the original OP info intact below for reference as some of it may still be helpful but just know it is outdated.
***ORIGINAL POST FOLLOWS; ONLY RELEVANT FOR VIRGIN LBR20s ON THE ORIGINAL 2.5.2.20 (OR EARLIER) FIRMWARE***
Hi All,
I wanted to start a thread on the Orbi LBR20 as I have seen increased interest in it since release and I get a lot of questions about it. For those who aren't familiar with it or its capabilities they have posted a video unbox/overview of the unit on the Wireless Joint Facebook group which may be helpful to you: .
Of primary interest to most is the fact that it has both a Quectel Cat. 18 modem in it and runs a Netgear-customized version of OpenWRT Chaos Calmer (like other models in the Orbi line). The current firmware (2.5.2.20) also offers easy debugging and telnet access which makes bending the device to one's will relatively simple. With these details in mind, the following are a few FAQs I receive frequent PMs about that will hopefully be helpful to you:
Telnet/Root Access
At least on firmware 2.5.2.20, achieving command line access to the device is quite simple. Simply navigate to http://[IP_of_LBR20]/debug.htm and tick the box for 'Enable Telnet':

Once enabled you can simply use your favorite telnet client (I prefer Putty) to connect to telnet (port 23) on the device IP. Login using the same credentials you use to login to the web GUI.
Sending AT Commands to the Modem
There is no serial terminal software installed by default but one can easily echo commands to the AT port device ('/dev/ttyUSB2') and read the output with cat using one-liners in order to send useful commands to the modem. Be aware that syntax is very important here; graves accents surrounding the 'echo' command, return / new line characters following the actual AT command, and ensuring any double quotes required in a given AT command are escaped appropriately using backslashes are all imperative. Some examples of useful commands are noted below:
*** UPDATED 03/06/21. 'TTL_MOD' SCRIPT SIMPLIFIED; SWITCHED TO LOOPED SCRIPT FOR REGULAR INTERVAL EXECUTION***
Modifying IPTables, Blocking Auto Firmware Updates, and Disabling WiFi
As many who have hotspot limits will understand, it is very useful when a device has a full fledged copy of iptables installed and the Orbi definitely has this. While it is quite easy to add iptables rules over telnet to the device, it is another thing entirely to get those rules to persist after reboot or any interfaces changes.
Also, as was mentioned in the linked video overview of the device, Netgear has persisted with their stupidity in pushing firmware updates to devices without warning which can be a hassle for many reasons (not least of which is the quality of Netgear code and all their various product firmware bugs up to this point). So it would be nice to be able to block this 'feature' since we are in fact the owners of the device and not Netgear. Fortunately we can do this simply enough by either appending '/etc/hosts' or overwriting '/etc/resolv.conf' with a DNS server of our choosing that blocks access to the Netgear auto-update domain.
Finally, since my use case does not make use of WiFI on the Orbi, it would be nice to deactivate the radios on boot to save power and not add to all the existing RF congestion in my neighborhood; this can be done easily as well.
First the bad news: since the device reloads the root partition from ROM on every reboot we can't very well modify existing startup scripts under the root ('/') filesystem in the usual manner; we must be more creative here. The good news is that Netgear stores and runs the Armor (BitDefender) and Circle applications off of storage mounts which are persistent across reboots and not overwritten from ROM each time. Even if you don't have Armor or Circle enabled, there are some associated processes which load on every boot anyways so we can use these to 'piggy-back' off of in order to create and call a 'bootstrap' script containing the commands, or calls to additional scripts, that we want to be sure run on next boot if the device is powered down or restarted.
We will start by creating our main 'bootstrap' script. Turning off the WiFi radios is a single command under OpenWRT distros ('wifi down') so that will be an easy one-liner to add at the start of our bootstrap but I suggest including a 'sleep' for at least 60 seconds before taking wifi down so that we make sure the unit has finished loading first. Another useful task is blocking auto firmware updates by either modifying the DNS resolver or modifying the hosts file. This can be a simple one-liner in our bootstrap too. Finally we need a method to consistently enforce specific TTL values on the modem interface even during state changes (such as Ethernet interface link up/down); this is not so easily a one liner and would be helpful to run at a regular interval so we will create external scripts for this and add them to crontab via a few lines at the end of our 'bootstrap' script.
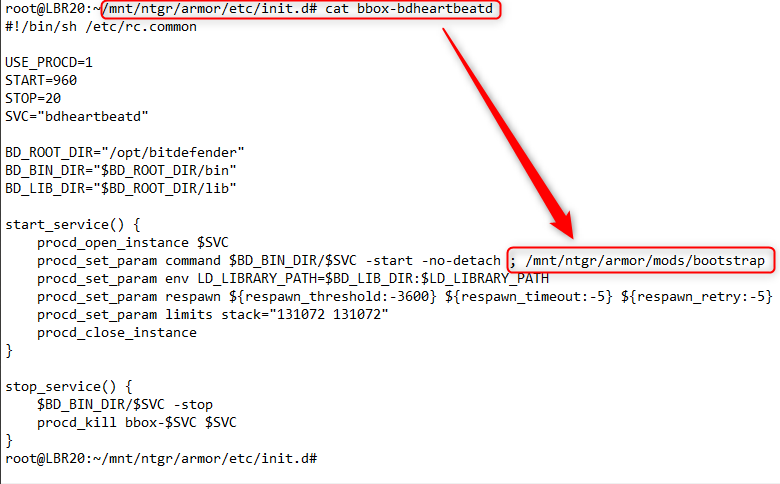
Under the existing folder for Netgear's Armor (/ntgr/mnt/armor/), we can create our own folder for 'mods' and underneath, the script files and crontab definition text file for the commands we we want to run (don't forget to 'chmod +x [filename]' to make any scripts executable!). The actual call to our bootstrap script will be made by simply appending a semicolon and its full path to the 'command' argument of 'procd_set_param' in the init.d script for the 'bbox-bdheartbeatd' daemon. The screenshot below illustrates how we modify the referenced line in the existing script:
Following are the scripts/files we have created:
'bootstrap' script
This runs one-time, one-liner commands such as turning off wifi and appending to hosts file to block auto firmware updates. It also creates cronjobs for everything that needs to run regularly. (We dump out the existing crontab to a temporary file, append it with our jobs, re-create the crontab, then remove our temporary file.)
'ttl_mod' script
This calls iptables and ip6tables commands to check for our mangle rules on the modem interface and add them if they are not found. Also blocks auto firmware updates.
From a workflow perspective, with these scripts/files in place a couple minutes after the next boot the host will disable WiFi and execute our 'ttl_mod' script every five minutes to block auto firmware updates and enforce our iptables mangle for both ipv4 and ipv6.
Sometime after the initial setup above, as an alternative to the hosts file method of blocking auto firmware updates, I instead decided to block them by adding 'devcom.up.netgear.com' to the deny list on my DNS server solution. Other DNS servers are similarly easy to exclude the domain in this way (Unbound, DNSMasq, Untangle, OpenDNS, etc.). Once I added the deny entry in NextDNS, I edited my 'bootstrap' script to remove the line appending '/etc/hosts' and instead to overwrite '/etc/resolv.conf' so that it would use NextDNS as opposed to the cellular provider's DNS servers. The Orbi device itself is using DNSMasq but only as a blind forwarder so it would be a bit more work to set the domain exclusion on the device rather than just changing its nameserver which is why I did it this way (please it's cool to keep tabs on any domains that the Orbi calls out to on its own and view them graphed out in NextDNS).
In case anyone was wondering I used the packet capture function from the same 'debug.htm' web page we used to enable Telnet from, in order to confirm with certainty (using Wireshark) what domain the firmware updates come from.

Quirks I've Noticed So Far
One annoyance I've encountered is that sometimes on bootup and attach to the cellular network, the DHCP on the WWAN0 interface (modem) gets a '192.168.0.1' address assigned to it along with DNS nameserver of '192.168.0.2' and subsequently my August Connect (WiFi bridge adapter for August smart lock products) stops connecting to August's servers (thus becoming unusable). I'm not exactly sure what is going on to cause this. It is kind of like how the old MR1100 IP Passthrough functionality breaks on some versions of its firmware. I thought maybe just my nameserver mod would allow the August Connect to resolve the August domain and that would resolve but it did not. The only 'fix' so far has been to reboot the LBR20 and then the next network attach shows it using the standard T-Mobile DoD reserved address space with my modded nameserver selected. Given this issue only occurs sometimes when I have to reboot the device it is not a showstopper for me but I thought it worth sharing in case others were having issues with their 'smart' / IoT products.
Megathread?
That's all I have to share for now but I hope others will add replies with tidbits they have found useful in their use of the LBR20. Hopefully we can get a nice 'megathread' going which will be a useful source of info to other LBR20 owners. I will come back to this and update as I come across new info or delve into more mods with this device. I have reached out to the developer of the famed Voxel firmware for other Netgear routers and inquired about creating a bounty for the creation of Voxel firmware for this device since it's based on a similar SoC to other Orbi devices; have not heard anything back yet but it would be a very cool possibility to have a fully modern build of OpenWRT with package support while still retaining any proprietary bits/integrations required for the nice modem and WiFi connectivity. A guy can dream, right? Unfortunately I won't have enough time to delve into such an undertaking myself.
***UPDATED 10/7/20***
Cell Locking In my testing this week I've found I have a tower broadcasting two, adjacent cell IDs. One is on B66 (B4) and gets 2xCA (B66 PCC w/ B2 SCC) but the speed falls off more during periods of congestion. The other is on B2 and gets 3xCA (B2 PCC w/ B66 & B71 SCCs). I was able to confirm the CA combos with AT+QCAINFO. The latter seems generally less congested sometimes coming in at 2x the DL speeds of the former during times of peak load. The frustrating part was that the LBR20 kept wandering back to the B66 cell whenever the winds would change and the signal would be ever so slightly stronger than the B2 cell. Thus I found it helpful to lock the modem to the faster cell. This can be done with AT+QNWLOCK.
Sadly, the LBR20 does not have the newer, more stable syntax of AT+QNWLOCK="common/lte", it only has the legacy AT+QNWLOCK="common/4g" which Quectel admins claim "may have issues" (https://forums.quectel.com/t/lte-cell-p ... -ec25/3581). Nevertheless, the command seems like it works fine from my testing. Just need to obtain the EARCFN and PCID of the cell you wish to lock to first with AT+QENG="servingcell" and/or AT+QENG="neighbourcell" (the former if you're actively connected to the desired one, the latter if you're not). Once you have those, you can run AT+QNWLOCK="common/4g",1,[EARCFN],[PCID]. In my case (see side note below code block about entering the command):
As a side note I've noticed that even with escaping double quotes etc., the QENG command does not like to return output by catting the modem device while sending the command with 'echo -e' like all the other commands I ran so far. So, for at least issuing AT+QENG commands, I open two telnet sessions, in the first I run 'tail -f /dev/ttyUSB2' and in the second I issue the command with 'echo -e "AT+QENG=\"servingcell\"\r\n" > /dev/ttyUSB2'. This setup appears to work reliably:

***UPDATED 01/15/21. THE FOLLOWING SECTION MAY BE GENERALLY INTERESTING/USEFUL BUT I LATER FOUND MY CA DROPOUTS TO BE CAUSED BY T-MOBILE/SPRINT MERGER TOWER CHANGES IN MY AREA AND I NO LONGER RUN THIS SCRIPT SINCE IT BECAME DISRUPTIVE TO RUN AT ANY REGULAR INTERVAL AND ATE UP DATA WITH ALL THE SPEEDTESTS*** ̶*̶*̶*̶U̶P̶D̶A̶T̶E̶D̶ ̶1̶0̶/̶8̶/̶2̶0̶*̶*̶*̶
"Expiring" CA Quirk on T-Mobile
For whatever reason after what seems like an arbitrary amount of time (but usually between 12 and 24 hours), my local T-Mobile tower seems to cease honoring carrier aggregation during downloads. AT+QCAINFO will still show 3xCA (B2 PCC, w/ B66 and B71 SCCs) but a speedtest quickly reveals only the PCC is actually active (download speed will not break 100Mbps which is a dead give away in my setup that only one band is in use). A detach and reattach to the network restores CA abilities in short order (accomplished by AT+CGATT=0, followed by AT+CGATT=1, with about a 15-20 second gap in between to wait for the detach to complete). Given I don't care to manually run speedtest all day and detach/reattach to the network when CA seems to drop off, I have automated this with the following script which can be added to our 'cronjobs' definition file to be called at regular intervals: 'ca_chk' script
So as you have probably gathered by looking at the text of "ca_chk", we have hijacked the built-in Ookla API configuration to check our connection speed once per hour (starting 10 minutes after initial boot of the router). If the speed is less than 100Mbps (you can change that value to suit your situation more appropriately), the modem performs a detach/reattach to the network to restore full CA throughput then copies the speedtest result back to our persistent storage with a filename that indicates the detach/reattach occurred. If the speed is fine, the result file is simply moved over to persistent storage with a filename indicating only a test was performed but no detach/reattach took place.
------------------------------------------------------------------------------------------------------------------------------------------------------
VOXEL FIRMWARE V9.2.5.2.29.1SF-HW RELEASED
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 2.29.1.zip
Release notes can be downloaded here:
https://www.voxel-firmware.com/Download ... 1SF-HW.log
VOXEL FIRMWARE V9.2.5.2.29SF-HW RELEASED
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 9SF-HW.zip
VOXEL FIRMWARE V9.2.5.2.28S.1F-HW RELEASED
!!! Please upgrade to this version ASAP as there are many security vulnerabilities patched !!!!
Updated version of Voxel firmware is out and can be downloaded below:
https://www.voxel-firmware.com/Download ... 1SF-HW.zip
Release notes can be found here:
https://www.snbforums.com/threads/custo ... -hw.76775/
Also in this version is 'get-sms.sh' a tool for reading SMS messages. If you can test the tool and report any issues, this would be most appreciated. Usage below:
Code: Select all
get-sms.sh - read all SMS
get-sms.sh #num - read SMS #num
get-sms.sh #start #end - read SMS from #start to #end.***VOXEL V9.2.5.2.23.1SF-HW***
Voxel has made a new revision already which includes improved QCA WiFi drivers taken from Netgear stock v2.6.5.2. This should improve WiFi performance for those that use WiFi on the LBR20:
https://www.voxel-firmware.com/Download ... 1SF-HW.zip
This was done for the RBK50 as well. More details can be found here;
https://www.snbforums.com/threads/custo ... ost-700398
***VOXEL FIRMWARE IS HERE!***
https://www.voxel-firmware.com/Download ... 3SF-HW.zip
That's right folks! The legend himself has applied his optimization skillz to the LBR20. Being the first Voxel release for the LBR20 I would like get as many LBR20 owners who can test it as possible so we can provide valuable feedback and support for future revisions. Also, please consider donating some $$$ if you are are happy with his work as I know for a fact he had to pay over $650 USD of his own money in his country to obtain an LBR20 in order to compile firmware for it. This has not yet been announced in the SNB forums as he would like some extended testing which I told him we would be happy to provide
Netgear's latest stock firmware (2.6.4.2+) includes more encryption for Netgear's internal HTTPS certs which makes the source firmware harder to work with and it provides no real feature enhancements. Thus, this first release is based off of the popular 2.5.2.20 stock firmware GPL sources and has been tested to run just fine with A05 and A06 LTE (Quectel) modem firmware (tested by me on T-Mobile/Sprint). Because it is built on 2.5.2.20 source, it is recommend to flash to Netgear 2.5.2.20 prior to flashing Voxel's firmware otherwise softbrick could occur requiring TFTP recovery (https://kb.netgear.com/000059634/How-to ... ndows-TFTP).
Voxel firmware V9.2.5.2.23SF enhancements vs Stock:
- Many component packages updated
- Various Netgear bugs fixed
- Many CVEs are patched including very serious CVE-2019-11477 and CVE-2019-11478 (kernel)
- OpenSSL compiled to leverage hardware acceleration (crypto engine) along with ASM acceleration; up to 8x faster than stock
- Modern compiler was used when building (9.4.0 vs. 5.2.0 used by Netgear). Cortex-A7 specific compiler flags used when compiling source (i.e. '-O2' and '-O3') and FPU functionality enabled vs. Netgear's generic ARM target and flags (i.e. '-Os'). This allows the firmware to take full advantage of hardware power which leads to faster performance all around as the unit is more responsive similar to Voxel firmware for the Orbi RBK50 (more details here: https://www.snbforums.com/threads/custo ... -hw.60308/).
- Ability to completely disable Netgear Circle and Armor which frees up a great deal of resources for faster performance
- OpenVPN client and WireGuard clients added (no GUI, CLI-only ); Voxel has tested WG but I have not yet as I do not have a WG server spun up at the moment
- Up-to-date Dropbear SSH server is running by default allowing secure root access out of the box
- Fully functioning overlay filesystem under '/mnt/circle' which allows for modification and addition of files which cannot be easily changed on stock firmware. Example: creating '/mnt/circle/overlay/etc/rc.local' allows us to make our own 'rc.local' for things which we want executed on startup.
- Netgear 'net-wall' binary replaced by custom script which calls original binary but allows use of custom firewall and direct iptables rules easily as well. Leveraging circle overlay we can create '/mnt/circle/overlay/opt/scripts/firewall-start.sh' which can include our own iptables rules which will execute on each interface state change (i.e. should not get wiped out by other Netgear processes; exception to this is PDP or APN changes which *do* require a reboot or re-execution of 'firewall-start.sh' to add back iptables rules lost by Quectel connection manager reconnection upon PDP or APN changes).
- Updated CIFS package for 'mount' command which allows the mounting of CIFS network shares (i.e. Windows PC or SMB share from NAS) for use with Entware packages etc. (ex. mount.cifs //192.168.1.100/DiskC /mnt/share -o user=username,iocharset=utf8,vers=3.02)
- Accelerated OpenVPN Server (the one available in GUI)
- DNSCrypt Proxy-2 and stubby
- Adding Orbi satellites (i.e. RBS20 etc.)
- Armor (BitDefender) and Circle (but we all know these are crap, resource hogs anyways better handled by other purpose-built devices/software and not shoehorned into a router)
- Filesystem '/mnt/circle' is only 26MB so cannot install larger things on it like Entware packages (thus the example to use CIFS mount for Entware storage on another file server)
Code: Select all
Quick Start Guide
(!) IMPORTANT NOTE: it is strongly advised to update to the stock firmware 2.5.2.20
before flashing this version.
https://www.downloads.netgear.com/files/GDC/LBR20/LBR20_V2.5.2.20.zip
Warning:
I am not responsible for any damage of your router if you decide to try this custom
firmware. You should do all under your own risk and responsibility. Your router is
your router and you should understand the risk to brick it.
1. Flashing Voxel’s custom firmware build and rolling back to the stock.
Nothing special. The procedure is similar to flashing downloaded official stock
firmware. In general all your current settings (used in the stock firmware) should be
kept. But it is recommended to make the backup of your current settings before flashing.
Identically you can revert to the stock firmware.
2. Overlay partition on Circle partition.
Original stock firmware uses tmpfs overlay partition (in RAM). So all you changes in
the files/dirs are kept only until next reboot of router/satellite. If you need to keep
your changed/added files you should use /mnt/circle/overlay directory where you should
add your new or modified files keeping the dirtree of Orbi. For example, if you wish to
use your own /etc/dnscrypt-proxy-2.toml just place it into:
/mnt/circle/overlay/etc/dnscrypt-proxy-2.toml
3. Setting up ssh access to the router and satellite.
After flashing and your settings you may need to have SSH access to router. SSH daemon
dropbear in Orbi uses port 22 and accepts root login with your WebGUI password.
4. Open your own firewall ports.
If you need to make several ports accessible from WAN then create the text file
/mnt/circle/overlay/etc/netwall.conf with ports you need to open. Example of this file:
------------------------------------------------------------------------
ACCEPT net fw tcp 22,8443
ACCEPT net fw udp 1194
------------------------------------------------------------------------
(to open TCP ports 22 and 8443 and UDP port 1194).
NOTE: this file should contain LF symbol at the end of last line (press ENTER key in
your text editor).
Additionally you can use your own custom script to add your own iptables rules. This
script should be named firewall-start.sh and be placed in the:
/mnt/circle/overlay/opt/scripts/
directory, i.e. /mnt/circle/overlay/opt/scripts/firewall-start.sh with 755 permission
attributes (i.e. executable).
5. Enable DNSCtypt Proxy-2 or stubby.
To enable DNSCrypt Proxy-2 run from telnet console the commands:
nvram set dnscrypt2=1
nvram commit
reboot
To enable stubby run from telnet console the commands:
nvram set stubby=1
nvram commit
reboot
If both DNSCrypt Proxy-2 and stubby are enabled, only stubby will be used.
To disable DNSCrypt Proxy-2 or/and stubby set them to "0" by nvram.
6. Disable Armor (BitDefender) and Circle update startup.
To disable Armor update daemon run from telnet console the command:
nvram set noarmor=1
nvram commit
reboot
To disable Circle update daemon run from telnet console the command:
nvram set nocircle=1
nvram commit
reboot
7. Disable ReadyCLOUD (XAgent/XCloud).
To disable ReadyCLOUD update daemon run from telnet console the command:
nvram set nocloud=1
nvram commit
reboot
8. WireGuard client.
To start its using you should
(1). Prepare the text file in Unix format (https://en.wikipedia.org/wiki/Text_file#Unix_text_files)
with name wireguard.conf defining the following values: EndPoint, LocalIP, PrivateKey,
PublicKey and Port of you WireGuard client config from WG provider.
Example:
------------------------- cut here ---------------------------------------
EndPoint="wireguard.5july.net"
LocalIP="10.0.xxx.xxx/24"
PrivateKey="XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX="
PublicKey="XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX="
Port="48574"
------------------------- cut here ---------------------------------------
NOTE: no spaces before/after "=" symbol in example above.
NOTE: the name of the file wireguard.conf is lowercase.
(2) Place this wireguard.conf file to /mnt/circle/overlay/etc/ directory. I.e.
/mnt/circle/overlay/etc/wireguard.conf
(3) Enter by ssh/telnet to your router (LBR20) and set the nvram variable wg-client
to 1
nvram set wg-client=1
nvram commit
(4) Reboot your router.
NOTE: to disable WireGuard client starting just set wg-client to "0" and reboot
the router.
9. OpenVPN client.
Important: only TUN clients are supported
To install OpenVPN client: just create /mnt/circle/overlay/etc/openvpn/config/client
directory and put your *.ovpn file (and CA/CERT/KEY if any).
See "Overlay partition on Circle partition".
You can start/stop OpenVPN client manually from telnet console for testing:
/etc/init.d/openvpn-client start
or
/etc/init.d/openvpn-client stop
to stop it. Log file for OpenVPN client is /var/log/openvpn-client.log, check it if you
have problems.
NOTE: you can add your own delay for starting OpenVPN client after reboot by the
command from telnet:
nvram set vpn_client_delay=120
nvram commit
(to set 120 sec. delay)
10. Mounting a CIFS Share.
It is possible to mount remote network share using the Common Internet File System (CIFS).
Example how to mount CIFS Share:
mkdir /mnt/share
mount.cifs //192.168.1.100/DiskC /mnt/share -o user=username,iocharset=utf8,vers=3.02
Voxel
As my last update from 2/18 indicated, router firmware v2.6.3.50 made some significant changes, chiefly disabling the ability to make changes on '/mnt/ntgr/...' which are reboot-persistent. Aside from the new router firmware version there is also a new LTE (Quectel modem) firmware version, A06. This modem firmware update was much more helpful than the router firmware as it appears to have improved modem stability on T-Mobile for me along with allowing the modem to connect to B41, which I did not see it do successfully before (B41 LTE may not be available in all markets). It works perfectly fine paired with 2.5.2.20 router firmware in my testing.
Digging into v2.6.3.50
Netgear seems to have finally stepped up their security game in fw v2.6.3.50 and, while that's a good thing in general, it has made modding a bit more difficult. As many have noticed already, the 'debug.htm' page with the checkbox for enabling telnet was removed and classic Netgear 'telnetenable' utilities do not work to enable telnet on this newer firmware either. This brings the LBR20 in line with the Orbi flagship products as most of those already lost [easy] telnet abilities in 2020 already. So, I had to crack open my dev unit and look for the jumper terminal pins I found while disassembling my original unit to see if they were indeed UART for accessing a serial console. After some fiddling with the pins and a multimeter I was off to the races at 115200 baud with an FTDI cable.
I was initially met with some frustration due to having TX and Ground reversed (and thus not being able to get any response to my keyboard inputs) but once I got that sorted I was greeted with a familiar Chaos Calmer root shell. From there I was able to confirm some relevant pieces of information that have changed in this new firmware. I won't list all my findings here but only those which are germane to our modem and iptables modding efforts:
- Armor/BitDefender filesystem ('/mnt/ntgr/..') is no longer listed in 'df' output; it is fully under the root ('/') filesystem which is mounted with overlay_fs (thus why nothing sticks after a reboot).
- The 'debug.htm' telnet functionality is not just hidden with javascript as it was in some other Orbi product firmware last year, the functionality to enable telnet at all from the web gui ('net-cgi' function calls) has been completely removed as far as I can tell.
- The 'telnetenable' daemon *is* still listening on port 23/UDP as revealed by 'ps' list of its running process and an nmap scan. Many had surmised that it wasn't listening since it does not respond to telnetenable 'magic packets' sent to enable 'telnetd' (telnet daemon) on 23/TCP. Packet captures and strace confirmed it would receive the packet but it was discarded and no 'ACK' was returned.
- 'telnetenable' daemon binary has been changed. It's file size was larger and it appears to have been compiled with a newer GCC toolchain. An strace revealed it is also checking magic packet authentication password values against 'http_passwd_hashed' which is an unsalted SHA256 hash of the classic, plaintext 'http_passwd' (aka, the web gui 'admin' password set when you first setup the router).
- Despite modifying telnetenable clients to send magic packets with an SHA256 hash of the 'admin' password, the daemon would still not respond to enable requests. After some professional assistance from a master reverser (thank you, Bjoern!) it was determined that Netgear has now customized the Blowfish encryption algorithm of telnetenable. This was why magic packets got no response since all the telnetenable client programs/scripts thus far only support the standard Blowfish implementations. The reverser was able to use these findings to create a new telnetenable client which sends successful magic packets to the LBR20 (and likely other Orbi routers as well).
Other Goodies Found
Found some other 'hidden' goodies so far in the new firmware web interface as well. Here is an inventory that might be worth further exploration by folks who have the time and/or interest:
- hidden_info.htm
Nice summarized info page of device settings. Of particular interest is the ability to 'select' specific modem carrier firmware. I haven't been brave enough to select something from the dropdown to test but I'm curious if it would switch to the selected MBN and restart the modem. Hope someone brave tests this and reports back
- hidden_manual_set_ant.htm
Appears to allow manual config of the *WiFi* antenna array in the unit.
- currentsetting.htm
Summarized setting info from the unit.
- debuginfo.htm
Some very basic info from the unit. Seems mostly useless at present.
- POT.htm
Some basic uptime info?
- DEV_device_info.htm
A bit more detailed device info overview.
- LED_light_info.htm
Some info about the current LED lights' state.
***IMPORTANT NOTE 02/18/21***
Coming out of hibernation for a moment to post a warning for Netgear LBR20 owners: the latest firmware (2.6.3.50) appears to change the partition structure making the Armor partition used to bootstrap custom scripts non-reboot-persistent. Also, telnet is not as easy to enable. I don’t have time to spend on engineering a solution to resolve this at present so recommend staying on older firmware for now. Can’t say I didn’t warn you . You can find the 2.5.2.20 firmware here in case Netgear pulls it but be aware that the filesystem changes that occur when moving beyond this version do not revert and '/mnt/ntgr/...' changes will still not persist on reboot unless you make some further partition modification manually:
https://drive.google.com/file/d/1Tc09ja ... sp=sharing
Finally, some of my original assumptions were wrong such as the unit not having serial terminal software installed (it does in fact have 'minicom'). I am leaving the original OP info intact below for reference as some of it may still be helpful but just know it is outdated.
***ORIGINAL POST FOLLOWS; ONLY RELEVANT FOR VIRGIN LBR20s ON THE ORIGINAL 2.5.2.20 (OR EARLIER) FIRMWARE***
Hi All,
I wanted to start a thread on the Orbi LBR20 as I have seen increased interest in it since release and I get a lot of questions about it. For those who aren't familiar with it or its capabilities they have posted a video unbox/overview of the unit on the Wireless Joint Facebook group which may be helpful to you: .
Of primary interest to most is the fact that it has both a Quectel Cat. 18 modem in it and runs a Netgear-customized version of OpenWRT Chaos Calmer (like other models in the Orbi line). The current firmware (2.5.2.20) also offers easy debugging and telnet access which makes bending the device to one's will relatively simple. With these details in mind, the following are a few FAQs I receive frequent PMs about that will hopefully be helpful to you:
Telnet/Root Access
At least on firmware 2.5.2.20, achieving command line access to the device is quite simple. Simply navigate to http://[IP_of_LBR20]/debug.htm and tick the box for 'Enable Telnet':
Once enabled you can simply use your favorite telnet client (I prefer Putty) to connect to telnet (port 23) on the device IP. Login using the same credentials you use to login to the web GUI.
Sending AT Commands to the Modem
There is no serial terminal software installed by default but one can easily echo commands to the AT port device ('/dev/ttyUSB2') and read the output with cat using one-liners in order to send useful commands to the modem. Be aware that syntax is very important here; graves accents surrounding the 'echo' command, return / new line characters following the actual AT command, and ensuring any double quotes required in a given AT command are escaped appropriately using backslashes are all imperative. Some examples of useful commands are noted below:
Code: Select all
cat /dev/ttyUSB2` echo -e "AT+CGSN\r\n" > /dev/ttyUSB2`
cat /dev/ttyUSB2` echo -e "AT +EMGR=1,7,\"012345678911121\"\r\n" > /dev/ttyUSB2`
cat /dev/ttyUSB2' echo -e “AT+QCFG=\"band\",0,2000,0,1\r\n” > /dev/ttyUSB2`Modifying IPTables, Blocking Auto Firmware Updates, and Disabling WiFi
As many who have hotspot limits will understand, it is very useful when a device has a full fledged copy of iptables installed and the Orbi definitely has this. While it is quite easy to add iptables rules over telnet to the device, it is another thing entirely to get those rules to persist after reboot or any interfaces changes.
Also, as was mentioned in the linked video overview of the device, Netgear has persisted with their stupidity in pushing firmware updates to devices without warning which can be a hassle for many reasons (not least of which is the quality of Netgear code and all their various product firmware bugs up to this point). So it would be nice to be able to block this 'feature' since we are in fact the owners of the device and not Netgear. Fortunately we can do this simply enough by either appending '/etc/hosts' or overwriting '/etc/resolv.conf' with a DNS server of our choosing that blocks access to the Netgear auto-update domain.
Finally, since my use case does not make use of WiFI on the Orbi, it would be nice to deactivate the radios on boot to save power and not add to all the existing RF congestion in my neighborhood; this can be done easily as well.
First the bad news: since the device reloads the root partition from ROM on every reboot we can't very well modify existing startup scripts under the root ('/') filesystem in the usual manner; we must be more creative here. The good news is that Netgear stores and runs the Armor (BitDefender) and Circle applications off of storage mounts which are persistent across reboots and not overwritten from ROM each time. Even if you don't have Armor or Circle enabled, there are some associated processes which load on every boot anyways so we can use these to 'piggy-back' off of in order to create and call a 'bootstrap' script containing the commands, or calls to additional scripts, that we want to be sure run on next boot if the device is powered down or restarted.
We will start by creating our main 'bootstrap' script. Turning off the WiFi radios is a single command under OpenWRT distros ('wifi down') so that will be an easy one-liner to add at the start of our bootstrap but I suggest including a 'sleep' for at least 60 seconds before taking wifi down so that we make sure the unit has finished loading first. Another useful task is blocking auto firmware updates by either modifying the DNS resolver or modifying the hosts file. This can be a simple one-liner in our bootstrap too. Finally we need a method to consistently enforce specific TTL values on the modem interface even during state changes (such as Ethernet interface link up/down); this is not so easily a one liner and would be helpful to run at a regular interval so we will create external scripts for this and add them to crontab via a few lines at the end of our 'bootstrap' script.
Under the existing folder for Netgear's Armor (/ntgr/mnt/armor/), we can create our own folder for 'mods' and underneath, the script files and crontab definition text file for the commands we we want to run (don't forget to 'chmod +x [filename]' to make any scripts executable!). The actual call to our bootstrap script will be made by simply appending a semicolon and its full path to the 'command' argument of 'procd_set_param' in the init.d script for the 'bbox-bdheartbeatd' daemon. The screenshot below illustrates how we modify the referenced line in the existing script:
Following are the scripts/files we have created:
'bootstrap' script
This runs one-time, one-liner commands such as turning off wifi and appending to hosts file to block auto firmware updates. It also creates cronjobs for everything that needs to run regularly. (We dump out the existing crontab to a temporary file, append it with our jobs, re-create the crontab, then remove our temporary file.)
Code: Select all
#!/bin/sh
sleep 60
wifi down > /dev/null 2>&1
/mnt/ntgr/armor/mods/ttl_mod &'ttl_mod' script
This calls iptables and ip6tables commands to check for our mangle rules on the modem interface and add them if they are not found. Also blocks auto firmware updates.
Code: Select all
#!/bin/sh
while [ 1 ]
do
# IPv4 TTL mod
iptables -t mangle -C POSTROUTING -o wwan0 -j TTL --ttl-set 65 > /dev/null 2>&1 || \
iptables -t mangle -I POSTROUTING 1 -o wwan0 -j TTL --ttl-set 65
# IPv6 TTL mod (prevents leaks not covered by IPv4 rules)
ip6tables -t mangle -C POSTROUTING -o wwan0 -j HL --hl-set 65 > /dev/null 2>&1 || \
ip6tables -t mangle -I POSTROUTING 1 -o wwan0 -j HL --hl-set 65
echo "127.0.0.1 localhost http.fw.updates1.netgear.com devcom.up.netgear.com" > /etc/hosts
sleep 300
doneSometime after the initial setup above, as an alternative to the hosts file method of blocking auto firmware updates, I instead decided to block them by adding 'devcom.up.netgear.com' to the deny list on my DNS server solution. Other DNS servers are similarly easy to exclude the domain in this way (Unbound, DNSMasq, Untangle, OpenDNS, etc.). Once I added the deny entry in NextDNS, I edited my 'bootstrap' script to remove the line appending '/etc/hosts' and instead to overwrite '/etc/resolv.conf' so that it would use NextDNS as opposed to the cellular provider's DNS servers. The Orbi device itself is using DNSMasq but only as a blind forwarder so it would be a bit more work to set the domain exclusion on the device rather than just changing its nameserver which is why I did it this way (please it's cool to keep tabs on any domains that the Orbi calls out to on its own and view them graphed out in NextDNS).
In case anyone was wondering I used the packet capture function from the same 'debug.htm' web page we used to enable Telnet from, in order to confirm with certainty (using Wireshark) what domain the firmware updates come from.
Quirks I've Noticed So Far
One annoyance I've encountered is that sometimes on bootup and attach to the cellular network, the DHCP on the WWAN0 interface (modem) gets a '192.168.0.1' address assigned to it along with DNS nameserver of '192.168.0.2' and subsequently my August Connect (WiFi bridge adapter for August smart lock products) stops connecting to August's servers (thus becoming unusable). I'm not exactly sure what is going on to cause this. It is kind of like how the old MR1100 IP Passthrough functionality breaks on some versions of its firmware. I thought maybe just my nameserver mod would allow the August Connect to resolve the August domain and that would resolve but it did not. The only 'fix' so far has been to reboot the LBR20 and then the next network attach shows it using the standard T-Mobile DoD reserved address space with my modded nameserver selected. Given this issue only occurs sometimes when I have to reboot the device it is not a showstopper for me but I thought it worth sharing in case others were having issues with their 'smart' / IoT products.
Megathread?
That's all I have to share for now but I hope others will add replies with tidbits they have found useful in their use of the LBR20. Hopefully we can get a nice 'megathread' going which will be a useful source of info to other LBR20 owners. I will come back to this and update as I come across new info or delve into more mods with this device. I have reached out to the developer of the famed Voxel firmware for other Netgear routers and inquired about creating a bounty for the creation of Voxel firmware for this device since it's based on a similar SoC to other Orbi devices; have not heard anything back yet but it would be a very cool possibility to have a fully modern build of OpenWRT with package support while still retaining any proprietary bits/integrations required for the nice modem and WiFi connectivity. A guy can dream, right? Unfortunately I won't have enough time to delve into such an undertaking myself.
***UPDATED 10/7/20***
Cell Locking In my testing this week I've found I have a tower broadcasting two, adjacent cell IDs. One is on B66 (B4) and gets 2xCA (B66 PCC w/ B2 SCC) but the speed falls off more during periods of congestion. The other is on B2 and gets 3xCA (B2 PCC w/ B66 & B71 SCCs). I was able to confirm the CA combos with AT+QCAINFO. The latter seems generally less congested sometimes coming in at 2x the DL speeds of the former during times of peak load. The frustrating part was that the LBR20 kept wandering back to the B66 cell whenever the winds would change and the signal would be ever so slightly stronger than the B2 cell. Thus I found it helpful to lock the modem to the faster cell. This can be done with AT+QNWLOCK.
Sadly, the LBR20 does not have the newer, more stable syntax of AT+QNWLOCK="common/lte", it only has the legacy AT+QNWLOCK="common/4g" which Quectel admins claim "may have issues" (https://forums.quectel.com/t/lte-cell-p ... -ec25/3581). Nevertheless, the command seems like it works fine from my testing. Just need to obtain the EARCFN and PCID of the cell you wish to lock to first with AT+QENG="servingcell" and/or AT+QENG="neighbourcell" (the former if you're actively connected to the desired one, the latter if you're not). Once you have those, you can run AT+QNWLOCK="common/4g",1,[EARCFN],[PCID]. In my case (see side note below code block about entering the command):
Code: Select all
echo -e "AT+QENG=\"servingcell\"\r\n" > /dev/ttyUSB2
AT+QENG="servingcell"
+QENG: "servingcell","NOCONN","LTE","FDD",310,260,6C150D,222,1125,2,4,4,A6F7,-81,-8,-54,21,0,90,-
OK
echo -e "AT+QNWLOCK=\"common/4g\",1,1125,222\r\n" > /dev/ttyUSB2
AT+QNWLOCK="common/4g"
+QNWLOCK: "common/4g",1,1125,222
OK***UPDATED 01/15/21. THE FOLLOWING SECTION MAY BE GENERALLY INTERESTING/USEFUL BUT I LATER FOUND MY CA DROPOUTS TO BE CAUSED BY T-MOBILE/SPRINT MERGER TOWER CHANGES IN MY AREA AND I NO LONGER RUN THIS SCRIPT SINCE IT BECAME DISRUPTIVE TO RUN AT ANY REGULAR INTERVAL AND ATE UP DATA WITH ALL THE SPEEDTESTS*** ̶*̶*̶*̶U̶P̶D̶A̶T̶E̶D̶ ̶1̶0̶/̶8̶/̶2̶0̶*̶*̶*̶
"Expiring" CA Quirk on T-Mobile
For whatever reason after what seems like an arbitrary amount of time (but usually between 12 and 24 hours), my local T-Mobile tower seems to cease honoring carrier aggregation during downloads. AT+QCAINFO will still show 3xCA (B2 PCC, w/ B66 and B71 SCCs) but a speedtest quickly reveals only the PCC is actually active (download speed will not break 100Mbps which is a dead give away in my setup that only one band is in use). A detach and reattach to the network restores CA abilities in short order (accomplished by AT+CGATT=0, followed by AT+CGATT=1, with about a 15-20 second gap in between to wait for the detach to complete). Given I don't care to manually run speedtest all day and detach/reattach to the network when CA seems to drop off, I have automated this with the following script which can be added to our 'cronjobs' definition file to be called at regular intervals: 'ca_chk' script
Code: Select all
#!/bin/sh
sleep 600
while [ 1 ]; do
if [ "$(/bin/speedtest.sh run > /dev/null 2>&1 && grep "final result" /tmp/ookla_speedtest_result | awk '/download:/ {print $12}')" -lt "100000" ];
then echo -e "AT+CGATT=0\r\n" > /dev/ttyUSB2 ; sleep 20 ; echo -e "AT+CGATT=1\r\n" > /dev/ttyUSB2 ; mv -f /tmp/ookla_speedtest_result /mnt/ntgr/armor/mods/speedtest_reset_connection
else mv -f /tmp/ookla_speedtest_result /mnt/ntgr/armor/mods/speedtest_result
fi
sleep 3600
done
exit 0Re: Orbi LBR20 How-To / Megathread
Awesome! I just posted my response.hazarjast wrote: Wed Mar 23, 2022 8:21 amYes, this is good advice. Did not realize there was a troubleshooting section for Orbi. It will be good to post for help there to give more eyes to the issue. I replied to your post with some questions.egauk wrote: Mon Mar 21, 2022 11:33 am
I am having a very similar issue, but with the ATT tablet plan. I posted in this thread originally, but found a specific Orbi troubleshooting section and moved my post there. You may want to do the same.
viewtopic.php?p=24090#p24090
Re: Orbi LBR20 How-To / Megathread
What an amazing thing to wake up to this morning, that OP!!! It's like someone was ready my mind and saw all the chicken scratch notes I had been writing to myself through 300someodd posts!
@hazarjast
I read, reread, and reread again the OP, and I did end up with a couple questions. I'm sure it's because of my lack of knowledge of linux commands. I know just enough to get myself in trouble, so be kind if i should know this stuff.
My first questions is about whether some things that need to be ran at every boot.
1. bloatware (Armor/Circle/ReadyCLOUD/AWS IoT) ~ there are the scripts to run to shut them down, does this need to happen at every boot?
2. firewall-start.sh & firewall6-start.sh ~ We make the two files in /mnt/circle/overlay/opt/scripts, are these auto ran on boot up? Do these scripts need need to be added to the rc.local file?
3. wifi down ~ in this post viewtopic.php?p=20064#p20064 hazarjast has some code for shutting down all the wifi as they were using the lbr20 only as a way to get the internet into the house. Is this code still valid? And I'm assuming this would need to be ran at boot so a script put in /mnt/circle/overlay/opt/scripts, possible touch and chmod (see below) and then the file named in the rc.local file.
4. Blocking Auto Firmware Updates ~ in this post viewtopic.php?p=24108#p24108 they give this example of code, and says "'This calls iptables and ip6tables commands to check for our mangle rules on the modem interface and add them if they are not found. Also blocks auto firmware updates."
I know the newer method is to make 2 files, one for v4 and one for v6. Is there still a need to block auto updates?
4. /mnt/circle/overlay/etc/rc.local ~ in this file, is this where all boot up scripts are called from? Does this file need the touch and chmod ?(see below)
General questions:
5. firewall-start.sh & firewall6-start.sh making them it with 755 permission attributes (from the quick start guide) ~ do these files need the "touch and chmod +x" treatment like we did with the "celllock_mod"? My searching online find the "touch" may only be used when a file doesn't have content. And the "chmod +x" allows execute permission. It would seem that at least the chmod would need to be done.
I tried to be as clear as I could with all these, but I feel my lack of knowledge may hurt my explanations of things.
If I can explain something better let me know. I'm so excited to have this as an option now!!!


@hazarjast
I read, reread, and reread again the OP, and I did end up with a couple questions. I'm sure it's because of my lack of knowledge of linux commands. I know just enough to get myself in trouble, so be kind if i should know this stuff.
My first questions is about whether some things that need to be ran at every boot.
1. bloatware (Armor/Circle/ReadyCLOUD/AWS IoT) ~ there are the scripts to run to shut them down, does this need to happen at every boot?
2. firewall-start.sh & firewall6-start.sh ~ We make the two files in /mnt/circle/overlay/opt/scripts, are these auto ran on boot up? Do these scripts need need to be added to the rc.local file?
3. wifi down ~ in this post viewtopic.php?p=20064#p20064 hazarjast has some code for shutting down all the wifi as they were using the lbr20 only as a way to get the internet into the house. Is this code still valid? And I'm assuming this would need to be ran at boot so a script put in /mnt/circle/overlay/opt/scripts, possible touch and chmod (see below) and then the file named in the rc.local file.
4. Blocking Auto Firmware Updates ~ in this post viewtopic.php?p=24108#p24108 they give this example of code, and says "'This calls iptables and ip6tables commands to check for our mangle rules on the modem interface and add them if they are not found. Also blocks auto firmware updates."
I know the newer method is to make 2 files, one for v4 and one for v6. Is there still a need to block auto updates?
Code: Select all
#!/bin/sh
while [ 1 ]
do
# IPv4 TTL mod
iptables -t mangle -C POSTROUTING -o wwan0 -j TTL --ttl-set 65 > /dev/null 2>&1 || \
iptables -t mangle -I POSTROUTING 1 -o wwan0 -j TTL --ttl-set 65
# IPv6 TTL mod (prevents leaks not covered by IPv4 rules)
ip6tables -t mangle -C POSTROUTING -o wwan0 -j HL --hl-set 65 > /dev/null 2>&1 || \
ip6tables -t mangle -I POSTROUTING 1 -o wwan0 -j HL --hl-set 65
echo "127.0.0.1 localhost http.fw.updates1.netgear.com devcom.up.netgear.com" > /etc/hosts
sleep 300
done4. /mnt/circle/overlay/etc/rc.local ~ in this file, is this where all boot up scripts are called from? Does this file need the touch and chmod ?(see below)
General questions:
5. firewall-start.sh & firewall6-start.sh making them it with 755 permission attributes (from the quick start guide) ~ do these files need the "touch and chmod +x" treatment like we did with the "celllock_mod"? My searching online find the "touch" may only be used when a file doesn't have content. And the "chmod +x" allows execute permission. It would seem that at least the chmod would need to be done.
I tried to be as clear as I could with all these, but I feel my lack of knowledge may hurt my explanations of things.
If I can explain something better let me know. I'm so excited to have this as an option now!!!
Re: Orbi LBR20 How-To / Megathread
Well I seemed to answer a couple of my own questions while in a training about asset management, it was riveting!! 
And the "chmod +x" make a file executable, aka you can run it. This I had to do with the rc.local, and my wifi kill script. (i'm sure many people knew that, I did not )
)
I'm still not sure if I need to chmod +x to the firewall-start.sh and firewall6-start.sh files, and whether I need to call them up in the rc.local. My hunch says I do.
This would make zero sense to set all these and then instantly do a reboot. So I'm going to say these stay until something more than a simple reboot.mellow65 wrote: Thu Mar 24, 2022 11:51 am
@hazarjast
1. bloatware (Armor/Circle/ReadyCLOUD/AWS IoT) ~ there are the scripts to run to shut them down, does this need to happen at every boot?
I ran the code from this post, and magically all the wifi signals around me disappeared. I did have to do the chmod +x to the file to make it executable as it wouldn't run until i did that.3. wifi down ~ in this post viewtopic.php?p=20064#p20064 hazarjast has some code for shutting down all the wifi as they were using the lbr20 only as a way to get the internet into the house. Is this code still valid? And I'm assuming this would need to be ran at boot so a script put in /mnt/circle/overlay/opt/scripts, possible touch and chmod (see below) and then the file named in the rc.local file.
This would not run until i did the chmod +x on the file. Once I did it ran my script to kill the WIFI.4. /mnt/circle/overlay/etc/rc.local ~ in this file, is this where all boot up scripts are called from? Does this file need the touch and chmod ?(see below)
So I finally found the point of "touch", it's kind of like making a placeholder file with nothing in it. You essentially can achieve the same-ish thing by starting a nano file then saving with something in it. (I'm not sure if you can save a file with nothing in it in nano)General questions:
My searching online find the "touch" may only be used when a file doesn't have content. And the "chmod +x" allows execute permission. It would seem that at least the chmod would need to be done.
And the "chmod +x" make a file executable, aka you can run it. This I had to do with the rc.local, and my wifi kill script. (i'm sure many people knew that, I did not
I'm still not sure if I need to chmod +x to the firewall-start.sh and firewall6-start.sh files, and whether I need to call them up in the rc.local. My hunch says I do.
Re: Orbi LBR20 How-To / Megathread
1. Correct, 'nvram set' commands persist after reboot.mellow65 wrote: Thu Mar 24, 2022 5:01 pm Well I seemed to answer a couple of my own questions while in a training about asset management, it was riveting!!
This would make zero sense to set all these and then instantly do a reboot. So I'm going to say these stay until something more than a simple reboot.mellow65 wrote: Thu Mar 24, 2022 11:51 am
@hazarjast
1. bloatware (Armor/Circle/ReadyCLOUD/AWS IoT) ~ there are the scripts to run to shut them down, does this need to happen at every boot?
I ran the code from this post, and magically all the wifi signals around me disappeared. I did have to do the chmod +x to the file to make it executable as it wouldn't run until i did that.3. wifi down ~ in this post viewtopic.php?p=20064#p20064 hazarjast has some code for shutting down all the wifi as they were using the lbr20 only as a way to get the internet into the house. Is this code still valid? And I'm assuming this would need to be ran at boot so a script put in /mnt/circle/overlay/opt/scripts, possible touch and chmod (see below) and then the file named in the rc.local file.
This would not run until i did the chmod +x on the file. Once I did it ran my script to kill the WIFI.4. /mnt/circle/overlay/etc/rc.local ~ in this file, is this where all boot up scripts are called from? Does this file need the touch and chmod ?(see below)
So I finally found the point of "touch", it's kind of like making a placeholder file with nothing in it. You essentially can achieve the same-ish thing by starting a nano file then saving with something in it. (I'm not sure if you can save a file with nothing in it in nano)General questions:
My searching online find the "touch" may only be used when a file doesn't have content. And the "chmod +x" allows execute permission. It would seem that at least the chmod would need to be done.
And the "chmod +x" make a file executable, aka you can run it. This I had to do with the rc.local, and my wifi kill script. (i'm sure many people knew that, I did not)
I'm still not sure if I need to chmod +x to the firewall-start.sh and firewall6-start.sh files, and whether I need to call them up in the rc.local. My hunch says I do.
2. The 'firewall*' scripts are called whenever there's a call to reload the firewall rules. This can happen on startup, port state changes, disconnection/reconnection to the internet etc. Do NOT add them to rc.local.
3. I really wouldn't mess with the old post about killing wifi with fire. I never quite got that perfected. Just throw 'sleep 120 ; wifi down' in a script that you call from rc.local and call it good (waits 2 minutes after boot up and then kills the wifi radios). If you decide to use my half-baked commands from August I take no responsibility for anything it breaks
4a. No one has to worry about auto-updating firmware. Since Voxel is a different versioning scheme there will never be a Netgear firmware that would install itself. No need to refer to deprecated instructions.
4b. Yes, rc.local is the file that calls anything you want to run at startup. Touch or no touch does not matter as long as you create the overlay version of it at '/mnt/circle/overlay/etc/rc.local' (which replaces '/etc/rc.local' when you next reboot). Do not make this file executable (chmod +x); it's not necessary at all.
5. Yes, the 'firewall*' scripts should both be executable (chmod +x). Apologies, this was a miss on my part; I've gone back and added that instruction. Touch or no touch doesn't matter as long as you create the files and populate them with the appropriate content. Again, you should not be making rc.local executable; this is unnecessary. Any additional scripts you created like wifi kill script should be made executable.
You explained your questions well, hopefully my answers are clear and satisfactory
Re: Orbi LBR20 How-To / Megathread
not only was it clear and satisfactory, that got all my ducks in a row!!hazarjast wrote: Fri Mar 25, 2022 1:30 am
You explained your questions well, hopefully my answers are clear and satisfactory
Thanks again for all that you do/did. And sorry for all the questions, I'm just trying to write something up at a much lower level, maybe make a video, that I can share with my parents so they could walk through this step by step.
My last question (yeah right) that I will start reading through the code to see if I can follow along. Is your cell_lock_failsafe.sh code on github. If I wanted to try that, would I make a file in the script folder and call it in the rc.local?
Thanks again for all your hard work, you may never realize what it means to people like me who have been dealing with poor internet for far to long!!!
Re: Orbi LBR20 How-To / Megathread
No problem, glad it can be helpful to you.
Yes, if you want to try the failsafe script just create it in the ‘scripts’ overlay folder (/mnt/circle/overlay/opt/scripts/), make it executable (chmod +x) and call the actual file (/opt/scripts/script_name) from rc.local to run on startup.
Yes, if you want to try the failsafe script just create it in the ‘scripts’ overlay folder (/mnt/circle/overlay/opt/scripts/), make it executable (chmod +x) and call the actual file (/opt/scripts/script_name) from rc.local to run on startup.
Re: Orbi LBR20 How-To / Megathread
I have Calyx with a linkzone2. I've taken the SIM, done the magic, and TTL and put it in my LBR20. In order to not be throttled I have to use b2b.tmobile.com APN with ipv4 PDP. This combo doesn't work in the LBR20. Just in the linkzone. I can't tell from the linkzone2 which band I'm on which is part of the frustration. Any leads here? Is Tmob doing something funky to only allow the linkzone2 to connect with on the b2b APN?
Re: Orbi LBR20 How-To / Megathread
I was having problems with the T mobile home internet and only trying to run the ipv4, It would never connect. I had to switch it to ipv4v6 before things started coming up and working properly. No clue why, people said it should have worked. Maybe if you have ipv6 tables in voxel and not running ipv6 it geeks out somewhere. That's just a thought.
Re: Orbi LBR20 How-To / Megathread
I’m not sure why the link zone works with ipv4. Most of the TMO SIMs have received provisioning updates by now which only allow IPv4v6 or IPv6 only before an attach to the network can happen.
Re: Orbi LBR20 How-To / Megathread
Updated with some time stamps, because no one wants to listen to me talk for 40 mins!!hazarjast wrote: Fri Oct 02, 2020 10:44 am
If you are more of a visual learner, a fellow LBR20 user has created a very nice overview video covering most of what is included in this guide (I would still recommend reading through this guide in its entirety for completeness and understanding):
Re: Orbi LBR20 How-To / Megathread
Looking through the original post and using that spreadsheet, i'm getting
putting it in the command listed, is this what you're looking for?
I have not ran any of this, as it wouldn't work for me, but this is what coming up with.
Code: Select all
AT+QCFG="band",0,z420000000000000000putting it in the command listed, is this what you're looking for?
Code: Select all
echo -ne "AT+QCFG=\"band\",0,z420000000000000000\r\n" | microcom -X -t 1000 /dev/ttyUSB2You do not have the required permissions to view the files attached to this post.
Re: Orbi LBR20 How-To / Megathread
I'd like to use AdGuard Home installed on a machine on my local network as the DNS server, I've modified the /etc/stubby/stubby.yml file,
done:
nvram set stubby=1
nvram commit
reboot
But after reboot, the DNS is back to the ISP servers.
Also, the DNS settings in the UI do not seem to work.
Any help would be appreciated.
done:
nvram set stubby=1
nvram commit
reboot
But after reboot, the DNS is back to the ISP servers.
Also, the DNS settings in the UI do not seem to work.
Any help would be appreciated.
Re: Orbi LBR20 How-To / Megathread
Did anyone save the default bands for the Quectel EG18 modem? I had messed with some band locking long ago and want to get everything back to factory. I came across echo -ne "AT+QCFG=\"band\",0,42000001003300385a\r\n" | microcom -X -t 1000 /dev/ttyUSB2 but want to be sure that's the right one.
Re: Orbi LBR20 How-To / Megathread
I believe if you didn't save your bands out of the box, you're going to have to do a factory reset to get them back.jddebug wrote: Mon Apr 11, 2022 5:27 pm Did anyone save the default bands for the Quectel EG18 modem? I had messed with some band locking long ago and want to get everything back to factory. I came across echo -ne "AT+QCFG=\"band\",0,42000001003300385a\r\n" | microcom -X -t 1000 /dev/ttyUSB2 but want to be sure that's the right one.
But when i dumped mine, that's the number I got.
Re: Orbi LBR20 How-To / Megathread
If any one is interested, I recorded myself going through the 4 antenna mod. Now Ironically I stepped back a little because the cheapo antennas were not better than what came from the factory (shocking, I know). But I think it would be well paired with some quality antennas.
Re: Orbi LBR20 How-To / Megathread
Updated OP with latest Voxel firmware:
https://www.voxel-firmware.com/Download ... 0SF-HW.zip
Release Notes here:
https://www.snbforums.com/threads/custo ... -hw.78366/
https://www.voxel-firmware.com/Download ... 0SF-HW.zip
Release Notes here:
https://www.snbforums.com/threads/custo ... -hw.78366/
Re: Orbi LBR20 How-To / Megathread
Thanks for the video, it was really helpful for me. Thanks also for the command to get the signal strength for each antenna:mellow65 wrote: Wed Apr 13, 2022 12:55 pm If any one is interested, I recorded myself going through the 4 antenna mod. Now Ironically I stepped back a little because the cheapo antennas were not better than what came from the factory (shocking, I know). But I think it would be well paired with some quality antennas.
Code: Select all
echo -ne "AT+QRSRP\r\n" | microcom -X -t 1000 /dev/ttyUSB2Also, when using the two external antennas it disables the internal antennas and goes in 2x2 MIMO. How those the LBR20 detect this? Must the 4 antennas be the same for 4x4 MIMO and LBR20 detects that the internal and external antenna are not the same? Because at the end of @mellow65 setup he is basically reverting to the original antenna configuration (using 2 internal antennas and two external antennas). From my testing this configuration only use the two external antennas. When running the AT+QRSRP command I get two readings... So the performance should be worst than using 4 external antennas... I'm confused...
- Didneywhorl
- Posts: 3662
- Joined: Fri Mar 23, 2018 5:37 pm
- Location: USA
- Has thanked: 1379 times
- Been thanked: 770 times
- Contact:
Re: Orbi LBR20 How-To / Megathread
Put a load on the router with a video stream or other download or both, and mayb ea speed test, THEN run the command. Run it multiple times.gioele wrote: Thu Apr 14, 2022 1:38 pm ...
Thanks for the video, it was really helpful for me. Thanks also for the command to get the signal strength for each antenna:
But I’m still a bit confused with the internal antennas of the LBR20. I read that the LBR20 internal antennas are 4x4 MIMO. How is this possible if they only have two u.fl connectors? When running the AT+QRSRP commands with only the internal antennas I only see two readings… All this let me to believe that the internal antennas are 2x2 MIMO. Can someone confirm this?Code: Select all
echo -ne "AT+QRSRP\r\n" | microcom -X -t 1000 /dev/ttyUSB2
It will not enable 4x4 unless under demand, and even then if you are on a low freq band (B71, 5, 12, 13, 14, 17, 26, 29) it will not operate in 4x4.
Sometimes it may only return one number and the other 3 as 140 (default value).
Also, there are 4 U.FL connectors on the board for the LTE:
I'm not 100% sure it does disable them, but in general I believe it uses a cancellation circuit when an antenna completes the positive to negative circuit on the antenna port. If you look at the pcb you can see the jumpers on the pcb traces. I don't fully understand it but it's my best guess.gioele wrote: Thu Apr 14, 2022 1:38 pm Also, when using the two external antennas it disables the internal antennas and goes in 2x2 MIMO. How those the LBR20 detect this? Must the 4 antennas be the same for 4x4 MIMO and LBR20 detects that the internal and external antenna are not the same? Because at the end of @mellow65 setup he is basically reverting to the original antenna configuration (using 2 internal antennas and two external antennas). From my testing this configuration only use the two external antennas. When running the AT+QRSRP command I get two readings... So the performance should be worst than using 4 external antennas... I'm confused...
You do not have the required permissions to view the files attached to this post.
Re: Orbi LBR20 How-To / Megathread
Yeah confusion runs strong in my house too!! It's ok, and I wish i knew what I knew now when I started, but I messed up the plugs so I can't. But when i tried to put the plug back together with the parts that were on my desk, i found that when you install an antenna, it presses on a small internal spring and ungrounds those plugs. So essentially when there is no external antenna attached, those plugs are grounded and that's how the Orbi knows if there is something connected.gioele wrote: Thu Apr 14, 2022 1:38 pmThanks for the video, it was really helpful for me. Thanks also for the command to get the signal strength for each antenna:mellow65 wrote: Wed Apr 13, 2022 12:55 pm If any one is interested, I recorded myself going through the 4 antenna mod. Now Ironically I stepped back a little because the cheapo antennas were not better than what came from the factory (shocking, I know). But I think it would be well paired with some quality antennas.
But I’m still a bit confused with the internal antennas of the LBR20. I read that the LBR20 internal antennas are 4x4 MIMO. How is this possible if they only have two u.fl connectors? When running the AT+QRSRP commands with only the internal antennas I only see two readings… All this let me to believe that the internal antennas are 2x2 MIMO. Can someone confirm this?Code: Select all
echo -ne "AT+QRSRP\r\n" | microcom -X -t 1000 /dev/ttyUSB2
Also, when using the two external antennas it disables the internal antennas and goes in 2x2 MIMO. How those the LBR20 detect this? Must the 4 antennas be the same for 4x4 MIMO and LBR20 detects that the internal and external antenna are not the same? Because at the end of @mellow65 setup he is basically reverting to the original antenna configuration (using 2 internal antennas and two external antennas). From my testing this configuration only use the two external antennas. When running the AT+QRSRP command I get two readings... So the performance should be worst than using 4 external antennas... I'm confused...
Now, what I wish i would have tried before i messed it all up, was actually running a speed test while I had external antennas hooked up to the factory spots and running the QRSRP to confirm that it really was only showing 2 antennas working. Because now when I do that I get a reading on all 4. As you would possibly expect with a 4x4 set up.
My main reason why I went back was the cheap amazon antennas aren't amazing, and I was getting better results from the stock internal ones. If you're putting this in a proper antenna set up that's outside, that wont be an issue. This is just my testing and found the stockers aren't all that horrible all things considered.
Re: Orbi LBR20 How-To / Megathread
When I had the guts of a plug laying on the desk, I did find that it grounded out the plug if you didn't have anything hooked up to it.Didneywhorl wrote: Thu Apr 14, 2022 5:58 pm
I'm not 100% sure it does disable them, but in general I believe it uses a cancellation circuit when an antenna completes the positive to negative circuit on the antenna port. If you look at the pcb you can see the jumpers on the pcb traces. I don't fully understand it but it's my best guess.
I would be curious to see what running a speed test with something hooked up to the external ports gives you, are you still only pulling on 2, or does all 4 kick in.
Re: Orbi LBR20 How-To / Megathread
Thanks for the precision, this saved me lots of troubleshooting time! I moved the LBR20 to my cottage house and can now only connect to band 13 and operate in 2x2 with my 4 external antennas. Previously, at another location I was able to get 4x4. With only the 2 internal antennas I was never able to be in 4x4. The internal antennas only have two ufl connectors (1 and 3 in your photo). It is my understanding that they could never operate in 4x4 by themselves without external antennas.Didneywhorl wrote: Thu Apr 14, 2022 5:58 pm
It will not enable 4x4 unless under demand, and even then if you are on a low freq band (B71, 5, 12, 13, 14, 17, 26, 29) it will not operate in 4x4.
Re: Orbi LBR20 How-To / Megathread
From my testing, with the external antennas hooked up to the factory spots you can only get 2x2.mellow65 wrote: Thu Apr 14, 2022 7:46 pm I would be curious to see what running a speed test with something hooked up to the external ports gives you, are you still only pulling on 2, or does all 4 kick in.
I currently have 4 external antennas setup like the thumbnail of your video. Performance is not that great at my new location (not the same from my initial testing). I have antennas like yours. They are cheap 9bi gain antenna bought on amazon. The problem is that the LBR20 connects to the low frequency band 13 and operates in 2x2. I could have simply just connected two external antennas to the factory spots and the results would have been the same… My next step is to test if the two internal antennas perform better in my situation. I will test this when I go back to my cottage house in a few weeks. Since it seems that at this location, I’ll be in 2x2 no matter what, I pretty much opened the LBR20 for nothing… I even broke one of the wifi 5Ghz antenna by cracking open the case instead of “sliding” the case. Anyway, a lot of work for nothing but I learned a lot along the way!
Re: Orbi LBR20 How-To / Megathread
Have you bricked your device? Did a firmware fail to upload and you had no choice to yank the plug? Is the light just sitting there blinking mocking you, EFF YOU, EFF YOU.
I did.
This saved my bacon.
https://kb.netgear.com/000059634/How-do ... =000059634
If you don't have TFTP installed on your computer, try this.
https://teckangaroo.com/enable-tftp-windows-10/
I pushed the recommended firmware V2.5.2.20, took just seconds, and what a sign of relief!
Don't know if this fixes it all, but it saved me!!
I did.
This saved my bacon.
https://kb.netgear.com/000059634/How-do ... =000059634
If you don't have TFTP installed on your computer, try this.
https://teckangaroo.com/enable-tftp-windows-10/
I pushed the recommended firmware V2.5.2.20, took just seconds, and what a sign of relief!
Don't know if this fixes it all, but it saved me!!
Re: Orbi LBR20 How-To / Megathread
initially i was able to access ssh/telnet and to change the ttl and cell locking. i wanna tweak some of the settings but now i cant get access. i did check the enable telnet in the debug screen and still no go. "ssh: connect to host 192.168.1.1 port 22: Connection refused" is the msg i get on command prompt and with putty i still cant get access
Re: Orbi LBR20 How-To / Megathread
I'm gathering you posted on my video, if not crazy similarities.papaburr wrote: Thu Apr 28, 2022 11:05 pm initially i was able to access ssh/telnet and to change the ttl and cell locking. i wanna tweak some of the settings but now i cant get access. i did check the enable telnet in the debug screen and still no go. "ssh: connect to host 192.168.1.1 port 22: Connection refused" is the msg i get on command prompt and with putty i still cant get access
So I updated to the latest firmware this morning, and it went in just fine. I can SSH in via the command prompt/terminal still.
Now I'm sure I'll be corrected if I'm wrong here, but I have never once touched the telnet option. I feel that was an early on thing and not relevant to this working currently. As I haven't touched it and still able to mess around with it.
I originally thought maybe you weren't using command prompt as an admin, come to find out you don't need to.
Few questions come to mind,
Which port are you plugged into? I ask because there is an option to "Enable WAN/LAN1 port as LAN port", on mine by default it's checked, but I did have issues early on trying to use LAN1, and since then I have only used LAN2.
Can you ping the device? from command prompt "ping 192.168.1.1"
Can you log into the GUI?
Have you tried a "Revert to factory default settings"? This should not mess with your TTL or rc.local file including your tower lock file. I do believe you have to turn off the bloatware again and do the initial set up.
Have you downgraded to 29? If 30 is an issue for you, maybe try a lower firmware version.
Those are just some things that came to mind to try.
Re: Orbi LBR20 How-To / Megathread
so an update..that was me on the youtube comments. something must have changed cause i cant access root with command prompt or putty even though i orignally set it up thru command prompt. ive tried opeing port 22 and no go...eventually i saw someone mention enable telnet function in the debug menu..eventually found out thru comand prompt i can get access to the telnet part which was able to get root access. i still dont know how to edit any files thru the telnet (via vi) where when i was going thru command prompt (ssh function via nano) it was a breeze. i did reflash the voxel file thinking it had something to do with it. now i notice anytime the router gets unplugged it factory resets.. if i wanted to start from scratch can i reflash the stock firmware and thenteh voxel firmware?
Re: Orbi LBR20 How-To / Megathread
Yeah you can you flash the stock firmware. Keep in mind that isn't going to delete you TTL files, or any other scripts that you put in there. you may try to go backwards through the steps and delete things.
Re: Orbi LBR20 How-To / Megathread
Uh yeah that's super weird. I hope someone else can chime in, because mine does not do that.
Re: Orbi LBR20 How-To / Megathread
i did a 30/30/30 reset and it seem to help..maybe coincidence?? who knows im happy i dont have to reneter everything everytime. next question is VPN on this router?? or any tips on how to bypass tmobile video throttle..i can by running a vpn on the end device but would be awsome if i can run it thru the router
Re: Orbi LBR20 How-To / Megathread
Having difficulty performing Magic after a hardcore IMEI setting several weeks ago (AT+QPRTPARA=1). I need to change the IMEI back and I am getting an error after each magic command. Is there a way to reopen or revert back to the IMEI the device came with? I am able to perform other commands, do not understand why not allowing the command?? I have tried the factory reset without success.
-
nordicboy2
- Posts: 10
- Joined: Wed May 04, 2022 7:20 am
- Has thanked: 2 times
- Been thanked: 1 time
Re: Orbi LBR20 How-To / Megathread
Has anyone figured out how to do something similar with Voxel's firmware?outrage18 wrote: Fri Apr 09, 2021 12:37 am This custom DNS server example uses Google public DNS servers
In the /mnt/circle/mods directory, create a new resolv.conf file, that contains the IP addresses of your desired DNS servers
vi resolv.conf
Hit ‘a’ to append and paste in the following lines:
nameserver 8.8.8.8
nameserver 8.8.4.4
nameserver 2001:4860:4860::8888 # IPV6 wwan0
nameserver 2001:4860:4860::8844 # IPV6 wwan0
Write & Quit
Esc
:wq
Edit the ‘call_recurring’ script
vi call_recurring
Using arrow buttons, navigate to the end of the last line of the script, hit a to append from that location, hit enter twice to leave a blank line and start a new line then paste in the following
# This command periodically overwrites stock DNS servers with the ones you
# saved in the new resolv.conf file
cp /mnt/circle/mods/resolv.conf /tmp/resolv.conf
Write & Quit
esc
:wq
Reboot; give it a couple minutes after the LBR20’s WiFi link comes up and load up 192.168.1.1/adv_index.htm, you should see the Google IPv4 DNS servers, or the ones you choose to use under INTERNET PORT
The DNS settings on the web interface in 'Advanced' -> 'Setup' -> 'Internet Setup' -> 'Internet' are ignored (at least in V9.2.5.2.30SF-HW).
-
nordicboy2
- Posts: 10
- Joined: Wed May 04, 2022 7:20 am
- Has thanked: 2 times
- Been thanked: 1 time
Re: Orbi LBR20 How-To / Megathread
I found a solution to my own question about how to set custom DNS servers. My solution seems to work for now, but it is really ugly.
I created a script that runs at startup and continues to overwrite /tmp/resolv.conf every minute.
Hopefully someone else has a better solution than this or can foresee problems with this one.
/mnt/circle/overlay/etc/rc.local
/mnt/circle/overlay/opt/scripts/fixdns.sh
I created a script that runs at startup and continues to overwrite /tmp/resolv.conf every minute.
Hopefully someone else has a better solution than this or can foresee problems with this one.
/mnt/circle/overlay/etc/rc.local
Code: Select all
/mnt/circle/overlay/opt/scripts/fixdns.sh > /dev/null 2>&1 &
exit 0Code: Select all
while true;
do
sleep 60
/bin/cp /mnt/circle/mods/resolv.conf /tmp/resolv.conf
done